d0ctrine
Diamond
- Joined
- 17.08.24
- Messages
- 107
- Reaction score
- 4,189
- Points
- 93

Your VPN is your digital lifeline in this game. But commercial VPNs? Theyre about as trustworthy as a prison snitch. Today were diving into Tailscale - a mesh VPN that turns your dedicated servers into your own private network. No more trusting shady VPN providers wholl roll over the moment the feds flash a badge.
Why Tailscale?
Lets be real - commercial VPNs are a fucking joke. Youre basically paying some random company to spy on your traffic and hand it over to the feds when they come knocking. And dont even get me started on their "no logs" policies. Yeah right.
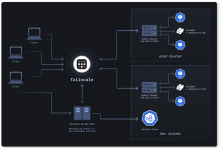
Enter Tailscale. This isnt your typical VPN - its a whole different beast. Instead of funneling your traffic through some shady data center in Romania, Tailscale lets you build your own private network between your machines. Its like having your own personal dark web, where you control every single node.
The beauty of Tailscale is in its simplicity and security. You're the boss - no sketchy VPN providers involved. It uses WireGuard encryption thatll make the NSA cry, with a distributed architecture that leaves no single point to compromise. Your keys rotate automatically to cover your tracks, and it plays perfectly with Tor when you need that extra layer of anonymity. Best of all? It integrates seamlessly with those dedicated servers youve already got running.
What Makes Tailscale Special?
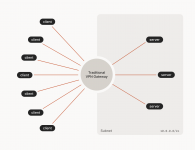
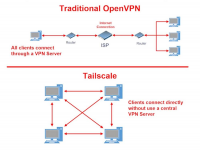
Most VPNs are like a digital funnel - everything goes through one central point that can be monitored, hacked, or seized. Tailscale says fuck that noise. It creates a mesh network where every device connects directly to the others through encrypted WireGuard tunnels.
This architecture is a game-changer for our kind of work. Theres no central server for the feds to raid, and since you control both ends, no one can snoop on your traffic. Your devices talk directly to each other through encrypted channels, and the whole thing works even behind firewalls without any port forwarding bullshit. The best part? Tailscale handles all the complex crypto stuff automatically, so you can focus on what matters - running your operation without leaving digital breadcrumbs everywhere.
Setting Up Your Tailscale Network
Step 1: Initial Setup
First things first - you need a Tailscale account. Heres the real shit about signup security:
- Burner email. ProtonMail works, or if youre feeling lazy, a disposable from Mailnesia, sign it up for a GitHub account and Sign it Up on the Tailscale site.
- A Dedicated Server Obviously - If you haven't read my guide on it, please read through
 Running and Hardening Your Own Dedicated Server
Running and Hardening Your Own Dedicated Server 
Pro tip: Generate an auth key in the admin console right after signup (by adding a Linux Server Device). Youll need this shit for your server setup - its way cleaner than trying to authenticate through a command line on a headless box.
Server Setup
SSH into your dedicated server and lets get this party started:
Code:
# Install this bad boy
curl -fsSL https://tailscale.com/install.sh | sh
# Now authenticate with that auth key you generated
sudo tailscale up --authkey YOUR_AUTH_KEY --advertise-exit-node
# Time to make your server actually route traffic
echo 'net.ipv4.ip_forward = 1' | sudo tee -a /etc/sysctl.conf
sudo sysctl -p
# Don't fuck up the firewall config
sudo ufw allow 41641/udp # Tailscale needs this port
sudo ufw reloadFinal Configuration
Heres where most tutorials leave you hanging, but Im not most teachers:
- Admin console
- Find your server under "Machines"
- Edit button
- Enable "Use as exit node"
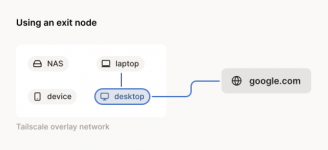
Without this step, your setup is as useful as a chocolate teapot. Your server might be running Tailscale, but it aint routing shit.
Client Setup
Now for your own machines:
- Download Tailscale for whatever OS youre running
- Install that shit
- Log in with your burner account
- Pick your exit node (the server you just set up)
- Watch your traffic flow through your own private tunnel
Going All In
[[[placeholder image: Image of a fortress-like server setup with multiple layers of security]]]
Want to take your security from "pretty good" to "fucking paranoid"? Let's talk about two nuclear options that'll make your server harder to crack than a meth head's teeth.
First up: Total Lockdown Mode. This is where you tell your firewall to block every goddamn connection except Tailscale traffic. Here's how:
Code:
# Block everything coming in
sudo ufw default deny incoming
# Only allow Tailscale traffic
sudo ufw allow in on tailscale0
sudo ufw allow out on tailscale0
# Flip the switch
sudo ufw enableNow your server's locked down tighter than a maximum security prison. Try hitting it from a regular IP - you'll get nothing but cold silence. Only your Tailscale connections get through that digital fortress.
But wait, there's an even more paranoid option: ditching Tailscale's central coordinator entirely. See, while Tailscale can't see your traffic, they still know who's connecting to what. For most of you baby carders, this trade-off is fine. But for those of you who break out in hives at the mere thought of trusting any company, meet Headscale.
Headscale is the "fuck you, I'll do it myself" version of Tailscale's control server. You host everything. No accounts, no third parties, no breadcrumbs leading back to any company's databases. It's the same mesh VPN magic, but you're running the whole damn circus.
I'm teaching you Tailscale first because it's training wheels for the real deal. Once you've got your head wrapped around how mesh VPNs work and you're ready to graduate to god-tier OPSEC, Headscale is your next move. Just remember: with great power comes great ways to fuck yourself over if you dont know what youre doing.
The Bottom Line
Running your own VPN network with Tailscale isnt just about dodging detection - its about building an infrastructure that gives you complete control over your digital footprint. This isnt some script kiddie shit with a commercial VPN and dreams of easy money. This is professional-grade tradecraft that separates the players from the prey.
Remember: In this game, the difference between paranoid and prepared is usually about 5-10 years in federal prison. The feds dont care about your excuses, they care about evidence. And right now, youre either building a fortress or digging your own digital grave.
Stay dangerous, stay smart, and never stop evolving. d0ctrine out.