d0ctrine
Diamond
- Joined
- 17.08.24
- Messages
- 107
- Reaction score
- 4,213
- Points
- 93
 A Rough Overview of Hacking in 2025
A Rough Overview of Hacking in 2025My inbox is overflowing with messages like d0ctrine teach me hacking! or d0ctrine how do I get credit card numbers from sites?. First off if youve been paying any damn attention to my other writeups youd know that before I was your favorite fraud guru I was a pentester. Yeah a legit certified get-paid-to-break-into-shit kind of pentester.

So yeah I know a thing or two about hacking shit. But lets get one thing straight: hacking in 2025 aint a walk in the park especially if youre looking to get into the carding scene. But since youre here and youre obviously too lazy to do your own research lets talk about hacking in 2025. This will be a rough overview of hacking in a new series where we focus on all things hacking.
Forget those Hollywood fantasies of hacking being some rapid-fire keyboard mashing with green code cascading down the screen. These days its a grind a constant chess match against ever-improving security. But for those with the guts the smarts and the sheer balls to take what they want theres still loot to be had.
Hacking: The Good Ol Days (Theyre Gone)
First off lets get real. Were not in the early 2000s anymore. Back then hacking was childs play. Websites were held together with duct tape and prayers running on ancient PHP and MySQL full of holes. Hacking was like taking candy from a baby.
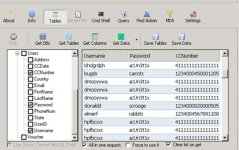
You could fire up Havij point it at a site and boom! Databases overflowing with credit card numbers. Or you could pwn a WHMCS install and suddenly have the keys to thousands of sites. Those were the glory days. Easy pickings.
But guess what? Those days are dead and buried. Websites wised up started using frameworks that didnt completely suck and patched up those embarrassing security flaws. And the real prize like credit card numbers and passwords started getting encrypted. So even if you did manage to break in youd be staring at a bunch of gibberish thatd take forever to crack without the decryption keys.
Vulnerabilities
So whats a wannabe hacker to do? You gotta grasp the basics. Hacking at its heart is about finding and exploiting vulnerabilities. Every system no matter how well-built has cracks. These cracks are vulnerabilities and they exist because nothing is perfect.

As developers pile on features and complexity the chances of introducing bugs skyrocket. These bugs can be anything from a minor hiccup to a gaping security hole.
Take SQL injection. Its a classic vulnerability where an attacker can inject malicious SQL code into an applications database queries. If the application isnt properly sanitizing user inputs (and many arent) an attacker can manipulate these queries to do all sorts of nasty shit like dumping the entire database or even taking control of the server.
The best part is that these vulnerabilities can be chained together to create a symphony of destruction. Let me give you an example:
You find a janky search feature on some companys website. Its vulnerable to SQL injection. With some digging you extract admin user session cookies from the database. These arent just any cookies - theyre your VIP pass to their internal admin panel.
Using these stolen cookies you waltz right into their admin dashboard. And what do you find? A file upload feature for product images. But these morons didnt properly validate file types. So instead of uploading cat pics you upload a sneaky PHP web shell disguised as an image.
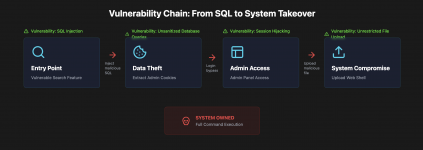
Game over. That innocent-looking image is a backdoor giving you full command execution on their server. From there you can worm your way deeper into their network escalate privileges or just trash their whole system. This is actually from my personal experience lol.
This isnt some Hollywood fantasy - its a real-world example of how one tiny crack (SQL injection) can lead to total system compromise. Each vulnerability is a stepping stone leading you deeper into the targets guts.
In 2025 hacking is less about targeting specific sites and more about finding vulnerabilities on a massive scale. Its like searching for a needle in a haystack except the haystack is the entire internet. This is where bug hunting comes into play and one tool has become indispensable for this: Nuclei.
Think of Nuclei as your automated vulnerability scout. Its an open-source tool that lets you define specific vulnerabilities youre looking for and then scan a shitload of targets to see if theyre vulnerable. Its like having a robot army that checks every door in every house in the world to see which ones are unlocked.

The beauty of Nuclei lies in its simplicity and its reliance on templates. These templates describe how to detect a specific vulnerability. Its like writing a recipe for finding a particular flaw.
Nuclei Templates: Recipes for Exploits
Each Nuclei template is a YAML file that contains:

- Metadata: Information about the vulnerability like its name severity and description.
- Request: The HTTP request(s) needed to test for the vulnerability. This is where you define what to send to the target.
- Matchers: Rules to determine if the target is vulnerable based on the response. This is where you define what to look for in the response to confirm the vulnerability.
Here's a simplified example of a nuclei template that checks for SQL injection vulnerabilities by testing common SQL injection payloads against parameters:
YAML:
id: sql-injection-test
info:
name: Basic SQL Injection Test
author: d0ctrine
severity: high
description: Tests for SQL injection vulnerabilities using common payloads
tags: sql,injection,vulnerability
requests:
- method: GET
path:
- "{{BaseURL}}/page.php?id={{payload}}"
payloads:
payload:
- "1' OR '1'='1"
- "1 UNION SELECT null,null--"
- "1' AND 1=1--"
- "' OR '1'='1"
matchers-condition: or
matchers:
- type: word
words:
- "SQL syntax"
- "mysql_fetch_array"
- "ORA-01756"
- "SQLite3::query"
condition: or
- type: status
status:
- 500
- 503This template sends SQL injection payloads to a parameter named 'id', then looks for common SQL error messages or specific HTTP status codes that might indicate a successful injection. It tests multiple payloads and considers it vulnerable if any matcher conditions are met.
How Nuclei Supercharges Bug Hunting
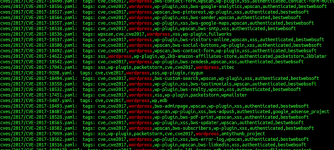
What makes Nuclei a godsend for hacking is its ability to quickly adapt to the latest vulnerabilities. As soon as a new exploit hits the scene the community jumps in to create a Nuclei template for it. This means you can start scanning for vulnerable systems almost immediately after a new vulnerability is disclosed.
For example lets say a new vulnerability is discovered in a popular WordPress plugin. Within hours someone will likely create a Nuclei template to detect it. You can then grab that template add it to your arsenal and start scanning the web for vulnerable sites.

This mass-scanning approach is the shit. Instead of painstakingly probing individual sites we can cast a wide net identify a large number of potentially vulnerable targets and then focus our efforts on the most promising ones. Its about efficiency and in this game time is money.
Youll also need to understand dorks. These are specific search queries you can run on Google Shodan or FOFA that can find vulnerable systems or sensitive info. For example a dork might reveal websites running a specific version of software with a known vulnerability. I covered some already here
Hacking for Cards
Now lets get to the good stuff: snagging those credit card numbers. There are a few ways to do this and none of them are a walk in the park.
Juicy Databases
First you could try to find shops that actually store credit card numbers in their databases. But heres the thing: most modern sites dont do that anymore. They use managed software like WooCommerce Shopify or Magento which tokenizes and securely relay card details to a payment processor via a secure iframe during checkout (think Stripe Elements Authorize.Net Adyen etc.).

Why? Because storing credit card numbers is a massive pain in the ass. Its a huge security risk and it makes you subject to all sorts of regulations like PCI DSS. Trust me no sane shop owner wants that headache. So youre left with dinosaur-age e-commerce sites that still store card numbers in their databases.
So how do you know if a site stores card numbers? Look for signs that theyre running their own custom e-commerce platform. Check the source code for clues look for unique checkout flows and try to identify the payment gateway theyre using. Its not foolproof but its a start.
Even if they do store cards theyre usually encrypted. But dont lose hope just yet. Since these cards are stored for future use (subscriptions recurring payments etc.) the application must have access to the decryption keys. A skilled hacker might be able to find and exploit these keys to decrypt the card data.
Sniffers
Even if the site doesnt store cards in their database they are still useful for carders as you can always inject sniffer scripts. This involves injecting malicious scripts into a websites checkout page to capture credit card details as theyre entered by unsuspecting customers. Its like a digital pickpocket silently stealing card numbers without the victim even knowing.

This technique is often associated with Magecart attacks which have become increasingly common. These attacks typically target e-commerce platforms particularly Magento and involve injecting malicious JavaScript code into the checkout process.
There are two main approaches to implementing sniffers on e-commerce sites:
1. JavaScript Sniffers: These are stealthy scripts injected directly into the checkout page that capture card data as its typed. Theyre harder to detect since they dont interfere with the normal payment flow. The downside? Modern security features like CSP (Content Security Policy) can make them tricky to implement.
2. Plugin/Phish Sniffers: If youve got admin access to a platform like WooCommerce you can install a malicious payment plugin. This swaps out the legit payment form for your own grabs the card details then smoothly redirects back to the real checkout. Less elegant than JS sniffers but sometimes its your only option when dealing with locked-down sites.

Ive written a detailed guide on implementing both types of sniffers complete with code examples and stealth techniques. You can find it here:
 The Self-Sufficient Carder: Your first CC Sniffer
The Self-Sufficient Carder: Your first CC Sniffer 
The key to a successful sniffer operation isnt just getting it installed - its staying undetected. Youll want to:
- Encrypt all stolen data before exfiltration
- Obfuscate your malicious code
- Use legitimate-looking domain names for data collection
- Blend your scripts in with normal site functionality
There are all sorts of tricks to make these sniffers hard to detect. You can obfuscate the code use encoding or even inject the script into a legitimate third-party library. But well get into that later.
The Human Element
These days systems are locked down tighter than a crabs ass so hackers are going after the weakest link: humans duh. Social engineering and buying access to enterprise platforms through logs have become major fucking attack vectors.
You dont need to be some elite coder to make it in this game. Shit if you can sweet-talk your grandma into giving you her secret cookie recipe youve got a shot. Sometimes a silver tongue can be more effective than a thousand lines of code. A well-placed bit of trickery can be worth more than a zero-day exploit these days. So where does a wannabe hacker start?

Well hacking groups are all over Discord and Telegram trying to weasel their way into company systems. Theyre not just looking for code exploits; theyre hunting for logs or other things that will give them access. They research a company – its sites panels subdomains – then scour logs for logins. Once theyve got a foot in the door they pivot. Sometimes they sweet-talk other employees playing on human weaknesses or sim-swap them to gain email access. Other times they find vulnerabilities in the internal network. Its a fucking mess but guess what? It works.

Remember most security efforts focus on customer-facing products. Developers often assume their internal tools are safe because theyre not publicly accessible. Thats a big fucking mistake. Groups like Lapsus$ have shown how devastating these attacks can be gaining access to major companies like Microsoft and Okta through compromised employee accounts. Its like walking through the front door because some moron left it unlocked.
Ransomware
Ransomware is another lucrative path and its often connected to the previous point about gaining access through social engineering or logs. Instead of going after small-time scores ransomware groups target entire companies. They encrypt the companys data and demand a hefty ransom for its release and a promise to not leak it to public.
These groups often operate on an affiliate model where individuals or smaller groups gain access to a companys network and then deploy the ransomware. The profits are then split between the affiliate and the ransomware operators.

Now if youre gonna go down this path at least have some damn morals. Dont target hospitals schools or other essential services.
More Resources
Here are a few resources to get you started:
- THE FUCKING GOAT:
- https://book.hacktricks.xyz/ (HackTricks - The Ultimate Pentesting Bible)
- Vulnerability Databases:
- https://nvd.nist.gov/ (National Vulnerability Database)
- https://www.exploit-db.com/
- https://cve.mitre.org/
- https://vuldb.com/
- https://www.rapid7.com/db/ (Rapid7 Vulnerability Database)
- Essential Tools:
- https://portswigger.net/burp (Burp Suite - Web Security Testing)
- https://github.com/sqlmapproject/sqlmap (SQLMap - SQL Injection)
- https://www.metasploit.com/ (Metasploit Framework)
- https://www.kali.org/ (Kali Linux - Pentesting OS)
- https://www.wireshark.org/ (Network Protocol Analyzer)
- https://nmap.org/ (Network Scanner)
- https://github.com/OWASP/ZAP (OWASP ZAP - Web App Scanner)
- Scanning & Reconnaissance:
- https://www.shodan.io/ (IoT Search Engine)
- https://fofa.info/
- https://github.com/projectdiscovery/nuclei
- https://censys.io/
- https://github.com/ffuf/ffuf (Fast Web Fuzzer)
- https://github.com/projectdiscovery/subfinder (Subdomain Discovery)
- Learning Platforms:
This is just a taste a little appetizer. Well dive deeper into specific topics in future installments of this series. And when I say deep I really mean it.
It Aint Easy But Its Possible
Look hacking in 2025 aint a walk in the park. It takes skill patience and a shitload of persistence. But if youre willing to put in the work learn the ropes and stay one step ahead theres still money to be made. Just remember its a constant cat-and-mouse game. The defenders are always adapting and so must you. As we continue with this series I will help you turn from a script-kiddie to someone with enough skills to hack your first site.

So are you ready to up your game? Or are you gonna stay a script-kiddie forever? The choice is yours.
Last edited: