d0ctrine
Diamond
- Joined
- 17.08.24
- Messages
- 107
- Reaction score
- 4,226
- Points
- 93

Buying cards is a fucking nightmare these days - you drop cash on premium cards just to get hit with declines or find out that same shits been resold 50 times over. Thats why I started the Self-Sufficient Carder series - to help you break free from relying on sketchy resellers and become your own source.
The truth is carding gets expensive with all the cards proxies and antidetect software. But having the skills to source your own cards gives you a massive advantage - cutting costs and keeping you independent from shops that could exit scam any day.

Disclaimer: The information provided in this writeup and all my writeups and guides are intended for educational purposes only. It is a study of how fraud operates and is not intended to promote, endorse, or facilitate any illegal activities. I cannot be held liable for any actions taken based on this material or any material posted by my account. Please use this information responsibly and do not engage in any criminal activities.
To Spam or Not To Spam?
Its a pure numbers game - blast enough emails and youll find marks ready to hand over their financial info. Modern tools let you target millions while staying under the radar. With basic social engineering you can craft messages that bypass filters and trigger that perfect mix of urgency and trust. Unlike other methods requiring constant adaptation spam fundamentals havent changed - people fall for the same psychological triggers they always have.
This Series
Ill be straight up - I spent weeks getting up to speed on modern spam techniques and testing what still works in 2024. While some aspects have evolved the core principles remain solid as fuck.Note: This series focuses purely on spam techniques. Phishing is its own beast that Ill cover separately. Here were focusing on getting your emails into inboxes at scale.
Were starting with technical concepts and psychology - the shit that makes or breaks a spam campaign. You can blast millions of emails but without understanding spam filters and what makes people engage youre just another script kiddie spraying garbage.
The series will be in three parts:
- core concepts and fundamentals
- practical step-by-step instructions for your first campaigns
- advanced techniques for bypassing security and scaling operations
No theoretical bullshit - just real working knowledge for mastering mass email delivery in 2024. This first part will only cover the fundamentals.
The Inbox
Lets strip away all the fancy bullshit and get down to the raw truth: spamming is about one thing and one thing only - getting your fucking email into someones inbox. Thats it. Thats the whole game.Not their spam folder. Not their promotions tab. Their actual fucking inbox sitting pretty right between Karens book club invite and their Amazon shipping notification. Everything else - the clever subject lines the spoofed domains the HTML formatting tricks - its all just supporting cast.
Think of it like breaking into a house. You can have the fanciest tools and plans but if you cant get through the front door youre just a sketchy fuck standing outside. Same with spam - all your brilliant scam ideas mean jack shit if your email gets nuked by spam filters.
Every decision you make should answer one question: Will this help my email reach the inbox? If not youre wasting your time.
Now lets look at the three pieces you need to actually pull this off.
Core Components
Your Sending Infrastructure
SMTP Servers
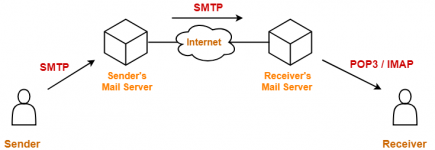
SMTP servers are the backbone of email delivery across the internet. They handle the routing and delivery of your spam campaigns. Mail providers track each servers reputation based on its sending history and IP address - this directly impacts whether you reach inboxes or not.
For SMTP servers you have several options. Carding hosting providers advertising clean IPs seem appealing until you discover most block port 25 and heavily rate-limit email sending. Even if you convince support to open ports theyll monitor your activity closely. A better approach is using compromised SMTP credentials from hacked servers and websites. Outdated WordPress installations and misconfigured business servers provide easy access. Botnet operators on Telegram sell access to thousands of these hacked relays at low cost. While some IPs may be flagged the cheap prices let you rotate through them quickly.
Remember: every SMTP has limits - daily caps hourly restrictions or bandwidth bottlenecks. After a few thousand emails most start queuing with delays of hours or even days. You need multiple SMTPs (at least 20-30) to handle serious volume. For a million-email campaign each SMTP should handle about 75k emails within 24-48 hours before the queues get too backed up.
Advanced spammers build their own SMTP infrastructure using bulletproof hosting or hijacked cloud accounts. It requires more initial setup but provides complete control. Hacked business email servers are particularly valuable - their established sending history translates to improved delivery rates for your phishing campaigns.
Domain Management
Your phishing domains need to look squeaky clean to mail providers. This means proper records and valid SSL certificates - all the technical bullshit that proves domain ownership and handles encryption. Without this foundation your phishing emails are dead in the water. Lack of these authentication mechanisms are also what makes email spoofing possible which makes your phishing campaigns actually more effective.
Email Spoofing
While not as effective as it was before due to modern security measures like DMARC this is where the moneys at - making your phishing emails look exactly like theyre from legitimate services. The old days of just changing the From header are long gone. Now youre dealing with SPF checking IP authorization DKIMs cryptographic signatures and DMARC tying it all together.
But there are always gaps to exploit. Some providers run weak DMARC policies or accept messages even when checks fail. Unprotected subdomains are another weakness - if the parent domains policies dont cover them youve got an opening. The holy grail is getting access to legitimate domains with working SMTP - their existing reputation gets your phishing past most security.
Cousin domains are another trick - registering domains that look identical to legitimate ones at first glance (paypa1.com vs paypal.com). Set these up right technically and theyll slip past both automated filters and human targets. When done properly your phishing lands looking identical to real service emails - thats how you get those sweet sweet bank details. Well cover detailed spoofing techniques in Part 2.
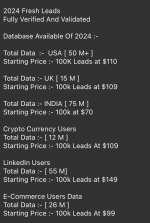
Your Email Lists (Leads)
Quality leads are fucking critical for phishing. Fresh email lists perform better and avoid detection. Old addresses just waste resources and get your infrastructure burned.
The best phishing lists include more than just emails. Want to hit PayPal users? A fresh list of emails confirmed to have PayPal accounts will convert way better than random addresses. Another perfect example is that a curated list of old peoples email addresses is pure phishing gold - theyre significantly more likely to enter their account and card details than some tech-savvy millennial. Match your leads to your phishing campaign for maximum conversion.
Mass Mailing Software
This is your command center. Premium tools like Atomic Mail Sender, and Advanced Mass Sender handle everything: server rotation phishing templates delivery tracking and blacklist monitoring. They distribute sends and randomize patterns to stay under the radar. The best ones juggle multiple SMTP servers automatically switching when one gets blocked and rotating between them to spread the load. They track delivery rates for each server and domain combo showing you which setups are landing in inboxes. Some even just run in an RDP making you use the RDPs server as your mail server although this is very ineffective.
Modern mailers support proxy integration to hide your real IP customizable HTML phishing templates and list cleaning to remove dead addresses. Some even test spam scores before sending and tweak content automatically to improve deliverability.
You need software that balances power with stealth. Basic tools blast in obvious patterns that get flagged instantly. Advanced mailers randomize delays vary message content slightly and distribute loads across servers to look like legitimate email patterns.
Modern Email Sending Platforms
Modern problems require modern solutions. While SMTP servers and mailer software remain solid options for experienced spammers 2024 brings us additional vectors - legitimate email platforms like Mailchimp SendGrid and Resend.
These platforms offer an alternative approach with built-in analytics established IP reputation and streamlined delivery systems. Instead of managing infrastructure yourself youre use their existing framework. Its not necessarily better than traditional methods - just different tools for different scenarios.
Well explore the ins and outs of these services in our upcoming guides. Each approach - whether traditional SMTP or modern platforms - has its own strengths. Smart spammers know when to use each tool in their arsenal.
Understanding Spam Filters
Another part you need to understand is what youre up against. Spam filters are your biggest enemy - theyre built to fuck up your entire operation before it starts.
Think of spam filters as bouncers at an exclusive club. They check everything about you before letting you in. Miss one check? Your ass is getting tossed into the spam folder.
Content Analysis
Your first challenge is making your message look legit:
- Words like FREE URGENT VERIFY in subject lines
- Obvious phishing links and malware attachments
- Too many images with barely any text
- Copy-pasting detected templates
Technical Verification
This is where most newbies fuck up:
- Using the same IP to blast thousands of emails
- Just registered your domain yesterday
- Missing proper SPF/DKIM/DMARC
- Half-assed header spoofing
Behavioral Patterns
Filters watch how you operate:
- Sending 10k emails in 5 minutes
- Recipients marking you as spam
- Using the same server for too long
- Reusing blocked IPs
Recipient Behavior
The final boss - actual human behavior:
- Real bank emails get read. Yours get deleted in 2 seconds
- High spam reports
- Nobody clicking your phishing links
- Zero people adding you to contacts
Remember: every failed campaign teaches you something. Modern filters are smart as fuck - they share intel like cops sharing mugshots. One mistake and youre burned. Take your time learn the patterns and always test before mass sending.
The Deep Rabbit Hole of Email Spamming
This guide covered the core fundamentals - the infrastructure technical requirements and defense systems needed to launch your first campaign. Without these basics youre just another script kiddie blasting garbage into void.
Whats Next?
In Part 2 of this series well dive into the practical side:
- Setting up your first mailing infrastructure from scratch
- Building targeted email lists that convert
- Crafting messages that bypass content filters
- Managing IP rotation and domain reputation
- Monitoring delivery rates and adjusting on the fly
- Scaling operations without triggering detection
Part 2 will walk you through launching your first campaign step-by-step from initial setup to your first successful delivery.
Email spam isnt for the weak. Youre going up against corporate security teams with endless resources. Every successful campaign is a victory but yesterdays tricks are tomorrows red flags. Adapt or die. Part 2 incoming. d0ctrine out.
Last edited: