
The truth is that Bitcoin isnt the privacy shield many think it is. If youre using it for anything shadier than buying socks youre playing with fire. This guide is about keeping your ass covered when transacting with the OG crypto.
We already covered Monero (in another forum) but lets be real - Bitcoin still dominates the underground economy. Problem is its got more holes than Swiss cheese when it comes to privacy. That blockchain? Its a map for anyone trying to track you down.

This isnt some basic "Bitcoin for Dummies" bullshit. Were kicking off a three-part series laser-focused on keeping your Bitcoin transactions anonymous as fuck.
Part one is all about side-channel attacks - the sneaky ways your opsec can fail even if youre being careful with your coins. Well cover how to create an airtight wallet that never leaks your info and why most of you idiots are probably broadcasting your location every time you check your balance.
By the end of the entire series youll have the knowledge to actually keep your transactions private or youll be too paranoid to use Bitcoin at all. Either way youre less likely to end up in cuffs.
This isnt just theory - its practical shit that could keep you out of a cell.
Time to get educated. Your freedom might depend on it.
P.S. Most of these apply to Litecoin too, just with minor differences.
How Bitcoin Works
You already know how Bitcoin works. You know it I know it even your grandma probably knows it by now. So we wont waste time on blockchain 101. Well dive into advanced blockchain analysis in the next installment.
For now were focusing on how transactions get pushed to the blockchain and where your wallet connects when youre moving coins. This is where most of you are leaving yourselves exposed.
Heres the deal: unless youre running your own Bitcoin node youre essentially trusting your privacy to some random server. Every time you open that wallet to check your balance or make a transaction youre connecting to a node somewhere. And that node sees your IP address transaction details and everything else youre doing.
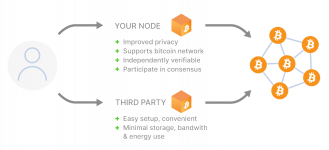
Most wallets connect to whatever node they feel like. Could be run by some pimply teenager in his moms basement or it could be a honeypot set up by the feds. You dont know which is which. Youre at the mercy of these services and hoping they wont roll over and expose your info the moment someone comes knocking
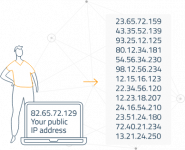
Think about it. Every transaction youve ever made every address youve interacted with, and all wallets addresses (even unused ones) - all tied to your IP. Its like leaving a trail of digital breadcrumbs leading straight to your front door.
Web wallets are even worse. If youre using one youre trusting a centralized service with all your transaction data and IP logs. Youre one subpoena away from having your ass fucked in a prison by Cabron.
The point is when youre not in control of how the node youre connecting to operates, youre not in control of your privacy. Youre vulnerable to having your entire Bitcoin history laid out for anyone to see.
And this even applies even if youre mixing your coins (which we will cover in the next installment) or exchanging them for privacy-oriented coins like Monero. Because the moment you transacted with a honeypot node, theres no turning back as they already have you logged.
Node Poisoning
You might think youre safe because youre not buying drugs on the darknet and youre just buying CVV. Think again. The feds and companies like Chainalysis are playing a whole different game - and youre the pawn.
Node poisoning is one of their weapon of choice. Heres how it works: they set up Bitcoin nodes all over the place. These nodes look legit and act as real nodes but theyre actually honeypots waiting to log every transaction that passes through them. Your IP address transaction details timing - all of it gets hoovered up and stored to a giant database ready to be combed through should they feel like tracking your specific wallet down.
Theyre running a massive swarm of poisoned nodes to capture data from SPV wallets. If theyre doing all this with Bitcoin, where every transaction is public, imagine what theyre trying also with Monero. Theyve already claimed to have deanonymized Monero transactions in Germany.
Remember that its not just about seeing who you sent coins to and how much. Theyre logging your IP address too. So now they can potentially link your Bitcoin address to your real-world identity. Congratu-fucking-lations youve just blown your own cover.
This gets even worse if youre using web-based wallets like BitPay or Coinbase Wallet. Youre basically handing over all your info on a silver platter. Might as well CC the FBI on all your transactions while youre at it.
The point is unless youre running your own node and taking serious precautions youre probably leaking more info than you realize. Every transaction could be another piece of evidence building a case against you.
Public Blockchain Lookups: A Fucking Trap
I know youre itching to check your balance or track a transaction. But using public blockchain explorers? Thats like walking into a police station to ask if theyre onto you yet.
Every time you punch your address into Blockchain.info, Blockchair, or any other public explorer, youre handing over your identity to the operators of these sites. These sites log everything - your IP, the addresses youre looking up, timestamps, your browser fingerprint, the whole thing.
You think that shits private? Think again. These companies are in bed with law enforcement. One subpoena and your entire Bitcoin history is laid bare, tied to your real-world identity.

The feds and Chainalysis have been pulling this shit with Bitcoin for years. Back in 2020, they were caught red-handed running a honeypot block explorer called WalletExplorer.com. This site was scraping users IP addresses and linking them to Bitcoin addresses. They even bragged to Italian cops about how it gave them "meaningful leads". And thats just the tip of the iceberg.
So whats the solution? Run your own fucking node. We covered this earlier, but it bears repeating. With your own node, you can query the blockchain all day long without leaving a trace. No third-party servers, no logs, no bullshit.
If you absolutely must use a public explorer (and I mean absolutely fucking must), at least have the sense to use Tor.
Hardening Your Wallet
The BTC blockchain might be public, but there are ways to blend in anonymously. Your first step is to harden your wallet and setup.
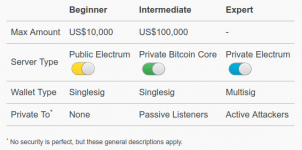
Heres a rough security cheatsheet by Sparrows Creator. As a carder, you must pick highest security possible (without affecting, or hassling your process too much) when deciding which tools and software you should use.
Sparrow or Wasabi: Your New Best Friends
Forget web wallets and exchange-provided bullshit. Sparrow and Wasabi are the way to go. Theyre open-source, feature-rich, and actually give a fuck about your privacy. Heres how to set them up right:
- Download Sparrow from sparrowwallet.com or Wasabi from wasabiwallet.io. Verify the PGP signatures, you lazy fucks.
- Install on a clean system. Ideally a dedicated machine that never touches your personal shit.
- Fire up Tor before you even think about opening either wallet.
- Open your chosen wallet and select "New Wallet". Choose a strong name that doesnt link to your identity.
- Back up your seed phrase offline. Write it down and hide it somewhere secure. Lose this and youre fucked.
- In settings, connect to your own node (more on that later) over Tor.
- Enable coin control features. This lets you manage your UTXOs for better privacy. We will get on this in the next installment.
The two wallets are roughly the same, but Wasabis got a leg up with built-in CoinJoin support - well get into that mixer shit in the next installment. For now, just know its there if you need it.
Running Your Wallet Behind Tor
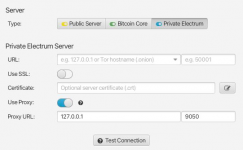
Using Tor with your wallet is essential. Heres how:
- Download Tor Browser Bundle from torproject.org.
- Install and run Tor before opening your wallet.
- In Sparrow, go to Tools > Settings > Server. In Wasabi, its in Settings > Network.
- Select "Use Tor" and "Use Separate Socks5 Proxy" (Sparrow) or just enable Tor (Wasabi).
- For Sparrow, set proxy to 127.0.0.1 and port 9150 (default Tor settings). Wasabi handles this automatically.
- Apply and restart. Your connections now route through Tor.
Running Your Own Node
This is the gold standard for privacy. Dont trust, verify. Basic setup:
- If youre ultra paranoid, get a dedicated machine. Raspberry Pi works fine, but a VPS is great too.
- Download Bitcoin Core from bitcoin.org.
- Install and start initial blockchain sync. This takes a while so be patient.
- Once synced, edit bitcoin.conf file to enable Tor connections.
- Add these lines to bitcoin.conf:
Code:proxy=127.0.0.1:9050 listen=1 bind=127.0.0.1 - Restart your node. Its now accessible only through Tor.
- In your wallet, connect to your node using its .onion address.
Heres the deal: with this setup, youve just made yourself a massive pain in the ass to track.
Your IP? Masked by Tor. Good luck tracing that shit.
Node poisoning? Irrelevant when youre running your own node. Youre verifying everything yourself, no trust required.
Side-channel attacks? Way harder now. Your wallets not constantly broadcasting your data to the feds.
The key here is separation. Your wallet doesnt know who you are, and neither does the network. As long as you dont fuck up and link your wallet to your real identity, youre basically invisible.
And remember, Wasabis got that CoinJoin feature built right in. Its like having a mixer on tap, ready to scramble your coins into oblivion. Well get into it in our next installment.
Conclusion
Alright you paranoid bastards, lets wrap this shit up. Weve covered the basics of hardening your Bitcoin setup, but dont get cocky. This is just the start and we have more to unpack in the future.

In our next installment, well dive deeper into blockchain analysis and how to counter even these advanced tracking techniques. Well cover mixing services, coinjoins, and other methods to further obfuscate your transactions on the blockchain. Youll learn how to make your transactions blend in like a chameleon at a rainbow party.
Stay tuned, because this rabbit hole goes way fucking deeper. The game of cat and mouse between privacy seekers and blockchain analysts never ends, and you need to stay ahead of the curve if you want to keep your ass out of the fire.
Remember, in this world, paranoia isnt a disorder - its a survival skill. Keep your guard up, your transactions private, and your identity separate from your coins. Class dismissed.
Last edited:

