d0ctrine
Diamond
- Joined
- 17.08.24
- Messages
- 107
- Reaction score
- 4,114
- Points
- 93

Welcome back ambitious bastards. If Pt 1 was the starter, then get ready for the main event of carding recon. Were about to get into the technical stuff that separates the noobs from the pros.
This part is all about Man in the Middle (MITM) tools like Caido and Burp Suite. These arent just fancy names - theyre the real deal for dissecting your targets defenses.

Well break down how these tools work, teach you to spot AI antifraud systems and payment gateways, and show you the ins and outs of HTTP packet tampering. By the end youll see websites in a whole new light.
Warning: this isnt for noobs. If youre still trying to figure out how to use a VPN you might want to build up your skills first. But if youre ready to level up, this guide is your ticket to really understanding the websites youre trying to hit.
So sit back and focus. Were about to get technical and class is in session. Advanced carding recon ahead.
Disclaimer: The information provided in this write-up is intended for educational purposes only. It is a study of how fraud operates and is not intended to promote, endorse, or facilitate any illegal activities. I cannot be held liable for any actions taken based on this material. Please use this information responsibly and do not engage in any criminal activities.
What are MITM Tools?
Burp Suite and Caido arent just fancy toys - theyre the scalpels youll use to dissect your targets.
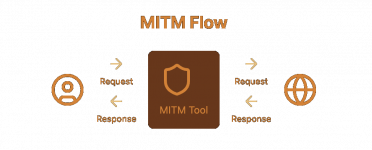
At their core, these tools work by inserting themselves between your browser and the target website. Every request you send and every response you receive passes through them first. Its like having a nosy bastard reading all your mail, except in this case, youre the nosy bastard.
Heres the basic flow:
- You type a URL into your browser
- Your browser sends the request to Burp/Caido
- Burp/Caido forwards the request to the website
- The website sends its response back to Burp/Caido
- Burp/Caido passes the response to your browser
But heres where it gets interesting for us carders. These tools dont just passively observe - they let you intercept, modify and even replay requests. Think of it as having a pause button for the internet.
Say youre scoping out a big e-commerce site. With Burp or Caido, you can:
- See exactly what data is being sent when you add items to your cart
- Identify what APIs are being called during checkout
- Spot any hidden fields or tokens used for fraud prevention
- Detect what kind of payment gateway theyre using
This intel is fucking gold for crafting your carding strategy. You can see precisely what info the site collects, how its formatted and where potential weak points might be.
For example, you might notice the site sends a "riskScore" parameter during checkout. Bingo - youve just identified part of their fraud prevention system. Or maybe you spot calls to a Stripe API. Now you know to use cards that havent been burned on Stripe-powered sites.
The real power comes when you start modifying requests. Changing parameters, altering headers, even injecting your own code - its all possible. This lets you test the sites defenses without actually placing orders. You can probe for weaknesses, see how the site reacts to unusual data and fine-tune your approach before risking a single card.
Setting Up Your Digital Scalpel: Burp Suite
Before we dive into the juicy stuff, you need to get your tools ready. Burp Suite is like the swiss army knife of web app hacking, and for us carders, its fucking essential. Heres how to set this beauty up:
- Download and Install: Head to PortSwiggers website and grab the Community Edition. Its free and packs enough punch for what we need. Once downloaded, install that shit.
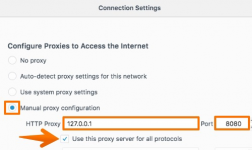
- Configure Your Browser: Were using Firefox for this guide cause its less of a pain in the ass with certificates. Open Firefox, go to Settings > Network Settings and set your proxy to manual. Use these settings:
HTTP Proxy: 127.0.0.1 Port: 8080
- Install BurpsCertificate: This is crucial. Without it, youll get more security warnings than a government whistleblower.
- Open Burp and go to https://burp
- Click "CA Certificate" in the top right
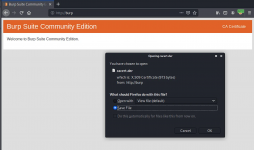 - In Firefox, go to Settings > Privacy & Security > Certificates > View Certificates
- In Firefox, go to Settings > Privacy & Security > Certificates > View Certificates
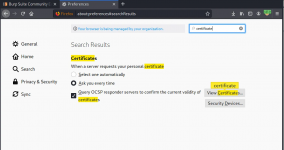 - Import the downloaded certificate and trust it for websites
- Import the downloaded certificate and trust it for websites
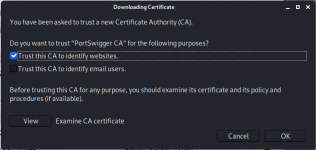
- Adding a SOCKS Proxy(Optional): If youre using a residential proxy heres how to chain it:
- In Burp, go to User options > SOCKS Proxy
- Enable SOCKS proxy
- Enter your proxy details
Now Burp will MITM your traffic and route it all through your SOCKS proxy. Slick, right?
Pro Tip: For initial recon, I usually just use a VPN set to the same country as the card Im planning to use. Its cleaner and less likely to raise flags. When its time to actually hit the site, thats when I switch to a full antidetect setup.
Mobile Recon: Yeah, you can do this shit on mobile too. Its a bit more involved and were not covering it today. Just know its possible and can be useful for sites with mobile-specific checks.
Now that youre locked and loaded, lets dive into the real shit. Time to start poking around those juicy targets.
Detecting AI Antifraud Analytics
Now that youve got Burp Suite locked and loaded, its time to put that shit to use. Before we dive in, make sure your Intercept is turned off in the Proxy tab. If its on, Burp will stop every request waiting for your input, and were not here to play 20 Questions with HTTP packets.
With Intercept off, Burp will silently record all traffic in the HTTP History tab. This is where the magic happens. As you browse your target site, youll see a flood of requests pile up here. Dont worry, well teach you how to make sense of this digital vomit.
Now, lets talk about the sneaky fuckers youre really after: AI-powered antifraud systems. These digital bloodhounds are all over modern e-commerce sites, sniffing out any hint of suspicious activity.
Modern e-commerce sites are filled with AI-powered antifraud systems. These fuckers work by injecting JavaScript into the page and monitoring everything from your mouse movements to your typing patterns.
As you go through Burps HTTP History, keep an eye out for these JavaScript files loading on the page. Theyre the calling cards of different antifraud systems:
- Sift Science: "https://cdn.sift.com/s.js"
- Signifyd: "https://cdn-scripts.signifyd.com/signifyd.js"
- Riskified: "https://beacon.riskified.com?shop=example.com"
- Forter: The exact URL can vary, but it often looks like "https://scripts.forter.com/forter.js" or "https://cdn.ftr-cdn.com/ftr/YOUR_SITE_ID.js"
- SEON: "https://cdn.seondf.com/js/v6/agent.js"
- Kount: "https://b.kount.net/collect/sdk"
- Ravelin: "https://cdn.ravelin.net/core/ravelin.js"
- ClearSale: "https://integration.clearsale.com.br/fp/check.js"
- Bolt: "https://connect.bolt.com/connect.js"
- Accertify: "https://h.online-metrix.net/fp/tags.js"
- PerimeterX: "https://client.perimeterx.net/PX_CLIENT_ID/main.min.js"
- Feedzai: "https://cdn.feedzai.com/v1/feedzai-fingerprint.js"
- Shape Security: "https://ds.shapesecurity.com/ds/client.js"
Finding those JS files is like finding a needle in a haystack especially on sites with a million scripts. A better idea is to keep an eye out for POST requests. Thats where the magic happens.
Remember this list isnt exhaustive. Antifraud tech moves faster than fashion trends. Always be on the lookout for suspicious JS files and network requests especially those loading from 3rd party domains. If you see something that looks like antifraud but isnt on this list, dig deeper.
These scripts collect a fuckton of data about your session. Theyre tracking:
- Device fingerprints
- Mouse movements and clicks
- Typing speed and patterns
- Time spent on page
- Browser plugins and settings
Browse through your target site, keep an eye on Burps HTTP History tab. Youll see POST requests to endpoints like "/api/risk/assess" or "/fraud/check" with all this data. Thats the antifraud system at work.
Here are a bunch of URLs for POST requests that monitor your sessions risk:
- Sift Science: "https://api.sift.com/v205/events"
- Signifyd: "https://api.signifyd.com/v2/cases"
- Riskified: "https://beacon.riskified.com/api/v2/beacon/collect"
- Forter: "https://api.forter-secure.com/v2/decisions"
- SEON: "https://api.seon.io/"
- Kount: "https://risk.kount.net/order.json"
- Ravelin: "https://live.ravelin.com/v2/sdk/event"
- ClearSale: "https://integration.clearsale.com.br/api/v2/order/create"
- Bolt: "https://api.bolt.com/v1/merchant/transactions"
- Accertify: "https://secure.accertify.com/CM/AccertifyMAWeb/OrderProcess"
- PerimeterX: "https://collector-PX_CLIENT_ID.perimeterx.net/api/v1/collector"
- Feedzai: "https://api.feedzai.com/v2/labels"
For example, if youre dealing with Sift Science, Burp will capture a request that looks something like this:
JSON:
{
"event": {
"$type": "$create_order",
"$user_id": "user123",
"$session_id": "abc123xyz",
"$order_id": "ORDER-123456",
"$amount": 10000,
"$currency_code": "USD",
"$billing_address": {
"$name": "John Doe",
"$address_1": "123 Main St",
"$city": "San Francisco",
"$region": "CA",
"$country": "US",
"$zipcode": "94111"
},
"$payment_methods": [
{
"$payment_type": "$credit_card",
"$payment_gateway": "$stripe",
"$card_bin": "424242",
"$card_last4": "4242"
}
],
"$shipping_address": {
"$name": "Jane Doe",
"$address_1": "456 Oak St",
"$city": "San Francisco",
"$region": "CA",
"$country": "US",
"$zipcode": "94110"
}
}
}This data is used to build a risk profile for your session. High risk scores trigger additional verification or straight-up rejections.
For some systems like Forter, the requests not show up until you initiate the payment. For cases like this you can look at requests to the main site and look for cookies like ForterToken, etc.
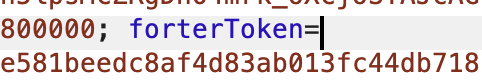
Booking.com Showing Riskified Token:

Identifying Payment Gateways
Finding the payment gateway is key to finding the right cards and methods. Heres how to expose these bastards:
Always start with a test card. Some popular test cards are:
- Stripe: 4242 4242 4242 4242
- Braintree: 4111 1111 1111 1111
- Adyen: 5555 4444 3333 1111
- Stripe: https://api.stripe.com/v1/payment_intents
- Braintree: https://api.braintreegateway.com/merchants/
- Adyen: https://checkoutshopper-live.adyen.com/checkoutshopper/
- CyberSource: https://secureacceptance.cybersource.com
- Authorize.Net: https://api.authorize.net/xml/v1/request.api
- WorldPay: https://secure.worldpay.com/jsp/merchant/xml/paymentService.jsp
Heres what a Braintree request might look like:
Code:
POST [url=https://api.braintreegateway.com/merchants/merchantid/client_api/v1/payment_methods/credit_cards]https://api.braintreegateway.com/merchants/merchantid/client_api/v1/payment_methods/credit_cards[/url]
{
"credit_card": {
"number": "4111111111111111",
"expiration_month": "12",
"expiration_year": "2025",
"cvv": "123"
},
"share": true
}And heres what a Stripe request looks like:
Code:
POST [url=https://api.stripe.com/v1/payment_intents]https://api.stripe.com/v1/payment_intents[/url]
{
"amount": 2000,
"currency": "usd",
"payment_method_types[]": "card",
"payment_method": "pm_card_visa"
}Some sites process payments on their own domain first. If you dont see direct calls to a known payment gateway, look for requests to the sites own API endpoints like "/api/process-payment" or "/checkout/finalize".
In these cases youll need to dig deeper. Look for telltale signs in the request parameters:
- "stripe_token" or "stripe_source" suggests Stripe
- "braintree_nonce" points to Braintree
- "adyen_encrypted_data" indicates Adyen
- "cybersource_token" implies CyberSource
- "authorize_transaction_key" hints at Authorize.Net
- "worldpay_order_code" suggests WorldPay
Remember, some sites use multiple payment gateways or route through intermediary services. Keep an eye out for services like:
Finding the payment gateway is just step one. Each gateway has its own quirks and potential vulnerabilities. Now you know which ones youre up against, you can fine-tune your approach and increase your chances of success.
Closing Thoughts
From setting up Burp Suite to spotting antifraud systems and unmasking payment gateways, you now have the tools to crack your targets like a pro.
Remember the more you know about a sites defenses the better you can tailor your attack. Dont just throw cards at a wall and hope something sticks. Use these techniques to craft a strategy that maximizes your chances of success.
But were not done yet. In our next guide well be diving into mobile recon. Well show you how to apply these same principles to mobile apps, a whole new playground for carding.
And well get our hands dirty with Burps Tamper tool. Youll learn how to modify requests on the fly, lower your fraud score by editing the values sent to the antifraud systems and slip past those AI dogs.
Until next time, keep your OPSEC tight and your skills sharp. Stay frosty.
Class dismissed. d0ctrine out.