Fixxx
Moder
- Joined
- 20.08.24
- Messages
- 1,060
- Reaction score
- 4,088
- Points
- 113
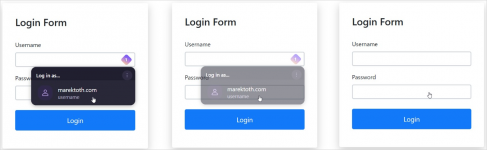
Cybersecurity specialists have discovered that six of the most popular password managers are vulnerable to clickjacking, allowing attackers to steal login credentials, 2FA codes and banking card data. The first to report on this issue was independent researcher Marek Tóth, who presented a report on vulnerabilities at the recent hacker conference DEF CON 33. Later, experts from Socket confirmed his findings, helping to notify affected vendors and coordinate the public disclosure of vulnerabilities. Tóth tested his attack on specific versions of 1Password, Bitwarden, Enpass, iCloud Passwords, LastPass, LogMeOnce and found that all browser versions can potentially leak confidential data in certain scenarios. Attackers can exploit these vulnerabilities when victims visit malicious pages or sites vulnerable to XSS attacks or cache poisoning. As a result, attackers gain the ability to overlay invisible HTML elements over the password manager's interface. The user will believe they are interacting with harmless clickable elements on the page, but in reality, they will trigger autofill, which will leak their confidential information to hackers. The attack is built around running a script on a malicious or compromised site. This script uses transparency settings, overlays or pointer-events to hide the browser password manager's autofill dropdown menu.
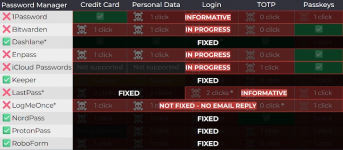
Although Tóth notified all manufacturers about the issues back in April and warned that public disclosure of vulnerabilities was planned for DEF CON 33, there was no quick response. Socket specialists contacted the developers again to remind them of the need to assign CVE identifiers to the issues in the respective products. Representatives of 1Password marked the researcher's report as informative, claiming that clickjacking is a threat that users themselves should protect against. LastPass developers also found the report informative and Bitwarden acknowledged the issues, although the company didn't consider them serious. Fixes were implemented in version 2025.8.0.
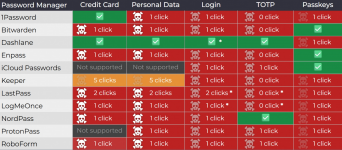
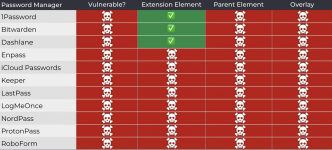
Neither Tóth nor Socket were able to contact LogMeOnce developers. Only after numerous media publications, LogMeOnce representatives informed that they had already prepared a patch. Currently, the following password managers, which together have around 40 million users, are vulnerable to clickjacking attacks:
To protect against such attacks, Tóth and Socket specialists recommend that users generally disable the autofill function in password managers and use only copy and paste.
Simultaneously, the attacker overlays fake and annoying user elements (such as cookie banners, pop-ups or CAPTCHAs) on the page. However, clicks on these elements hit the hidden password manager control elements, leading to the filling of forms with confidential information. Tóth demonstrated several DOM subtypes and exploitation variants of the same bug: direct manipulation of DOM element transparency, manipulation of root element transparency, manipulation of parent element transparency and partial or full overlay. He also demonstrated a method where the UI follows the mouse cursor and any user click, regardless of location, triggers data autofill. Tóth emphasized that the malicious script can automatically detect the active password manager in the victim's browser and then adapt the attack to the specific target in real-time.
As a result, the researcher tested 11 password managers for clickjacking vulnerabilities and found that all are vulnerable to at least one attack method.Although Tóth notified all manufacturers about the issues back in April and warned that public disclosure of vulnerabilities was planned for DEF CON 33, there was no quick response. Socket specialists contacted the developers again to remind them of the need to assign CVE identifiers to the issues in the respective products. Representatives of 1Password marked the researcher's report as informative, claiming that clickjacking is a threat that users themselves should protect against. LastPass developers also found the report informative and Bitwarden acknowledged the issues, although the company didn't consider them serious. Fixes were implemented in version 2025.8.0.
Neither Tóth nor Socket were able to contact LogMeOnce developers. Only after numerous media publications, LogMeOnce representatives informed that they had already prepared a patch. Currently, the following password managers, which together have around 40 million users, are vulnerable to clickjacking attacks:
- Enpass 6.11.6
- LastPass 4.146.3
- LogMeOnce 7.12.4
- Bitwarden 2025.7.0
- 1Password 8.11.4.27
- iCloud Passwords 3.1.25
"This is a well-known web attack technique that affects websites and browser extensions in general. Since the root problem lies in how browsers render web pages, we believe there is no comprehensive technical fix that browser extensions can implement on their own", 1Password stated, "noting that the extension already requires confirmation before autofilling payment information and in the next release, users will be able to enable similar warnings for other data types."
To protect against such attacks, Tóth and Socket specialists recommend that users generally disable the autofill function in password managers and use only copy and paste.
Additional Recommendations:
- Enable Two-Factor Authentication (2FA): Use 2FA wherever possible to add an extra layer of security to your accounts.
- Be Cautious of Phishing Attempts: Avoid clicking on suspicious links or visiting untrusted websites, as they can be vectors for clickjacking attacks.
- Keep Software Updated: Ensure that all your applications, including password managers and browsers, are up to date with the latest security patches.
- Use Reputable Password Managers: Stick to well-known password managers that have a track record of prompt security updates and responsive support.
- Review Security Settings: Periodically review and update the security settings of your password manager to ensure they are configured for maximum protection.