Fixxx
Moder
- Joined
- 20.08.24
- Messages
- 1,060
- Reaction score
- 4,088
- Points
- 113
Scammers are using Google services to send fake notifications about law enforcement requests on behalf of accounts.google.com. Imagine receiving an email notifying you that Google has received a subpoena from law enforcement demanding access to your account's content. The email looks quite "Google-like" and the sender's address is completely respectable: no-reply@accounts.google.com. This immediately triggers (at least) a slight sense of panic, doesn't it? And what luck - there's a link in the email to a Google support page where you can find out all the details about what's happening. The domain of the link also resembles the official one and, apparently, belongs to the real Google... You’ve probably guessed that this is a new phishing scheme. In it, scammers exploit several real Google services to confuse their victims and make the emails as believable as possible. Here’s a detailed breakdown.
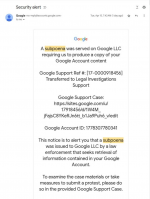
The email that initiates this attack is shown in the screenshot below - it convincingly pretends to be a notification from Google’s security system. The user is informed that the company has received a subpoena for law enforcement to access the content of their Google account.
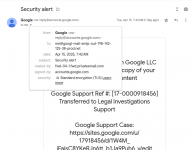
The sender's field (from) lists the legitimate Google address: no-reply@accounts.google.com. This is indeed the address from which security notifications are sent. The email also contains a couple of details that enhance its official appearance: Google account ID, support ticket number and a link to the case. Most importantly, the email informs the reader that if they want to know more about the case materials or contest the subpoena, they can do so via the link. Even the link looks quite plausible - the address includes the official Google domain and the aforementioned support ticket number. Only savvy users will notice the catch: all Google support pages are on support.google.com, while this link leads to a site on sites.google.com. However, the scammers are banking on users who are not familiar with such details. If the user is not logged in, clicking the link will take them to the real Google account login page. After logging in, they will be directed to a page on sites.google.com that successfully mimics the official Google support site.
It should be noted that the domain sites.google.com belongs to the legitimate service Google Sites. It was launched back in 2008 and is a fairly simple website builder. Nothing particularly special, but there is an important nuance: all sites created in it are automatically hosted under the google.com subdomain: sites.google.com. Such an address allows scammers not only to dull the vigilance of their victims but also to bypass various security systems - since both users and security solutions trust the Google domain. Therefore, it's not surprising that recently scammers have increasingly used Google Sites to create phishing pages.
The first sign that the reader may notice that the email is suspicious has already been described in detail above. It concerns the address of the fake support page: sites.google.com. More details that reveal the forgery can be found in the so-called header of the email. Phishing disguised as an official Google email: pay attention to the fields "to" and "mailed-by".
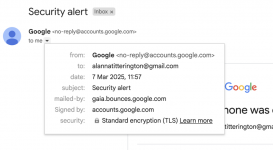
Here, attention should be paid to the fields "from", "to" and "mailed-by". In the from section, everything seems correct; the sender is listed as the official Google email: no-reply@accounts.google.com. However, just one line below, in the "to" field, there is not the real recipient's email address but something much more suspicious: me[@]googl-mail-smtp-out-198-142-125-38-prod[.]net. This address clearly attempts to imitate some "technical" Google address, but at first glance, the error in the company name is noticeable. Nothing like this should be in this field - it should contain the recipient's email address. Looking further, in the "mailed-by" field, we also encounter a suspicious address that is definitely not associated with Google: fwd-04-1.fwd.privateemail[.]com. In a genuine email, again, such nonsense cannot exist. Here’s how the corresponding fields look in a real Google security notification:
To understand how the scammers managed to send such an email and what they were after, cybersecurity researchers reproduced this attack. The investigation revealed that the criminals registered the domain googl-mail-smtp-out-198-142-125-38-prod[.]net (its registration has since been revoked) using the Namecheap service. Then, using the same service, they created a free email on this domain: me[@]googl-mail-smtp-out-198-142-125-125-38-prod[.]net. In addition, the criminals registered a free trial version of Google Workspace on the same domain. Next, they registered their own web application in the Google OAuth system and granted it access to their Google Workspace account. Google OAuth is a technology that allows third-party web applications to use Google account data for user authentication with the user's permission. You may have encountered Google OAuth as one of the authentication methods in third-party services: every time you click the "Sign in with Google" button, you are using this system. Additionally, an application can use Google OAuth to, for example, request permission to save files to your Google Drive. But back to our scammers. After registering the Google OAuth application, the service allows sending notifications to the email address associated with the verified domain. The administrator of the web application can manually enter any arbitrary text in the App Name field - this is what the criminals apparently took advantage of.
After this, Google sends a security notification from its official address with the specified phishing text. This email is sent to the scammer's email address with their domain, registered through Namecheap. This service, in turn, allows forwarding the received notification from Google to arbitrary addresses. All that is needed is to set a special condition and specify the addresses of potential victims.
In this case, it's not entirely clear what goals the criminals pursued by spreading this email. Authentication through Google OAuth doesn't imply that the victim's Google account credentials are transmitted to the scammers. During this process, a token is created that allows access only to certain data of the user's account, depending on the permissions granted by the user and the settings specified by the scammers. Judging by the content of the fake Google Support page that the deceived user lands on, the criminal's goal was to convince the victim to download certain "legal documents" supposedly related to their case. The nature of these documents is unknown, but it's quite possible that they contained malicious code. Researchers reported this phishing campaign to Google. The company acknowledged it as a potential risk to users and is currently working on fixing the vulnerability in OAuth. However, how long it will take to resolve the issue remains uncertain. To avoid becoming a victim of this and other elaborate phishing schemes, I recommend the following:
How the Phishing Email Masquerades as an Official Google Notification
The email that initiates this attack is shown in the screenshot below - it convincingly pretends to be a notification from Google’s security system. The user is informed that the company has received a subpoena for law enforcement to access the content of their Google account.
*the fraudulent email sent from no-reply@accounts.google.com masquerades as an official request for law enforcement.
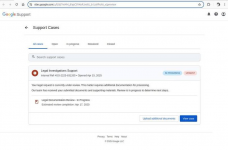
The sender's field (from) lists the legitimate Google address: no-reply@accounts.google.com. This is indeed the address from which security notifications are sent. The email also contains a couple of details that enhance its official appearance: Google account ID, support ticket number and a link to the case. Most importantly, the email informs the reader that if they want to know more about the case materials or contest the subpoena, they can do so via the link. Even the link looks quite plausible - the address includes the official Google domain and the aforementioned support ticket number. Only savvy users will notice the catch: all Google support pages are on support.google.com, while this link leads to a site on sites.google.com. However, the scammers are banking on users who are not familiar with such details. If the user is not logged in, clicking the link will take them to the real Google account login page. After logging in, they will be directed to a page on sites.google.com that successfully mimics the official Google support site.
*fake Google Support page, which the link in the email leads to.
It should be noted that the domain sites.google.com belongs to the legitimate service Google Sites. It was launched back in 2008 and is a fairly simple website builder. Nothing particularly special, but there is an important nuance: all sites created in it are automatically hosted under the google.com subdomain: sites.google.com. Such an address allows scammers not only to dull the vigilance of their victims but also to bypass various security systems - since both users and security solutions trust the Google domain. Therefore, it's not surprising that recently scammers have increasingly used Google Sites to create phishing pages.
How to Recognize a Fake: Detailed Information About the Email
The first sign that the reader may notice that the email is suspicious has already been described in detail above. It concerns the address of the fake support page: sites.google.com. More details that reveal the forgery can be found in the so-called header of the email. Phishing disguised as an official Google email: pay attention to the fields "to" and "mailed-by".
*note the "to" and "mailed-by" fields in the email header - they reveal the forgery.
Here, attention should be paid to the fields "from", "to" and "mailed-by". In the from section, everything seems correct; the sender is listed as the official Google email: no-reply@accounts.google.com. However, just one line below, in the "to" field, there is not the real recipient's email address but something much more suspicious: me[@]googl-mail-smtp-out-198-142-125-38-prod[.]net. This address clearly attempts to imitate some "technical" Google address, but at first glance, the error in the company name is noticeable. Nothing like this should be in this field - it should contain the recipient's email address. Looking further, in the "mailed-by" field, we also encounter a suspicious address that is definitely not associated with Google: fwd-04-1.fwd.privateemail[.]com. In a genuine email, again, such nonsense cannot exist. Here’s how the corresponding fields look in a real Google security notification:
*the "to" and "mailed-by" fields in a genuine Google security notification.
However, all these signs are quite difficult for the average person to notice, especially if they are frightened by the prospect of trouble with law enforcement. Even more confusion is added by the fact that the fake email is signed by real Google: accounts.google.com is listed in the signed-by field. In the next part of this post, we will explain how the criminals managed to achieve this and then discuss how not to become their victim.Step-by-Step Reconstruction of the Attack
To understand how the scammers managed to send such an email and what they were after, cybersecurity researchers reproduced this attack. The investigation revealed that the criminals registered the domain googl-mail-smtp-out-198-142-125-38-prod[.]net (its registration has since been revoked) using the Namecheap service. Then, using the same service, they created a free email on this domain: me[@]googl-mail-smtp-out-198-142-125-125-38-prod[.]net. In addition, the criminals registered a free trial version of Google Workspace on the same domain. Next, they registered their own web application in the Google OAuth system and granted it access to their Google Workspace account. Google OAuth is a technology that allows third-party web applications to use Google account data for user authentication with the user's permission. You may have encountered Google OAuth as one of the authentication methods in third-party services: every time you click the "Sign in with Google" button, you are using this system. Additionally, an application can use Google OAuth to, for example, request permission to save files to your Google Drive. But back to our scammers. After registering the Google OAuth application, the service allows sending notifications to the email address associated with the verified domain. The administrator of the web application can manually enter any arbitrary text in the App Name field - this is what the criminals apparently took advantage of.
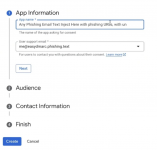
*Google OAuth allows for arbitrary web application names - this is exploited by scammers.
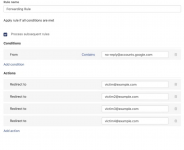
After this, Google sends a security notification from its official address with the specified phishing text. This email is sent to the scammer's email address with their domain, registered through Namecheap. This service, in turn, allows forwarding the received notification from Google to arbitrary addresses. All that is needed is to set a special condition and specify the addresses of potential victims.
*setting up a forwarding rule that allows sending a fake email to multiple recipients.
How to Protect Yourself from Such Phishing Attacks
In this case, it's not entirely clear what goals the criminals pursued by spreading this email. Authentication through Google OAuth doesn't imply that the victim's Google account credentials are transmitted to the scammers. During this process, a token is created that allows access only to certain data of the user's account, depending on the permissions granted by the user and the settings specified by the scammers. Judging by the content of the fake Google Support page that the deceived user lands on, the criminal's goal was to convince the victim to download certain "legal documents" supposedly related to their case. The nature of these documents is unknown, but it's quite possible that they contained malicious code. Researchers reported this phishing campaign to Google. The company acknowledged it as a potential risk to users and is currently working on fixing the vulnerability in OAuth. However, how long it will take to resolve the issue remains uncertain. To avoid becoming a victim of this and other elaborate phishing schemes, I recommend the following:
- If you receive a similar email, take a moment to carefully examine all the fields in the email header and compare them with genuine emails from Google. If you notice any suspicious discrepancies, feel free to send the email to the trash.
- Be Cautious with Google Sites. Treat websites on the google.com domain created using Google Sites with caution. Recently, scammers have increasingly used this service for various phishing schemes.
- Try never to click on links in emails, especially if they seem suspicious.
- Employ a robust security solution that will alert you to dangers and block access to phishing links in a timely manner.