d0ctrine
Diamond
- Joined
- 17.08.24
- Messages
- 107
- Reaction score
- 4,257
- Points
- 93

When I wrote
But it's not always rainbows and butterflies: lately people have been having problems setting up DNS on their antidetects. Often popular antidetects are having troubles resolving DNS properly leading to intermittent connections, often a lot of people even having trouble connecting in the first place. So today Im writing this guide to help everyone once and for all have clean and fast residential proxies.
The Theory
If you read through my previous guide about this the working theory is simple: we want proxy providers that block financial sites because this assures us that the proxies are unused in fraud and gives us an extremely higher chance in getting our from not getting blocked due to past history.

The problem is there isnt a singular way antidetect browsers manage DNS resolution, and this leads to a lot of people complaining and having issues with the method.
d0c's Proxy Script
Fuck relying on third-party software with a billion features when all you need is one goddamn thing. I got tired of watching newbies struggle with complex proxy setups so I built my own lightweight Python script that does exactly what we need - nothing more, nothing less.
This script sits between your browser and your proxy provider intercepting those DNS queries and routing them through Cloudflares 1.1.1.1 instead of whatever bullshit DNS your proxy provider forces on you. It's clean, efficient and doesnt require a PhD in networking to set up, and the best part: it works with every antidetect out there.
The beauty of this approach is its simplicity. No need to mess with system-wide network settings or fight with antidetect browsers' quirky implementations. Just run the script point your browser at the local port, and youve got pristine access to financial sites through clean residential IPs.
Here's the actual code that makes this magic happen:
Step-by-Step Guide to Install
Step 1: Install Python 3.13
- Open the Microsoft Store on your Windows computer
- Search for "Python 3.13" in the search bar
- Click on the Python 3.13 app from Microsoft or Python Software Foundation
- Click "Get" or "Install" and wait for installation to complete
- Once installed click "Open" or close the Microsoft Store
Step 2: Create a Project Directory
- Open Command Prompt (Press Windows+R, type "cmd" and hit Enter)
- Create a directory for the project:
Code:
mkdir C:\bindproxy
cd C:\bindproxy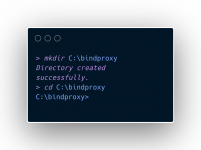
Step 3: Create a Virtual Environment
- Create a virtual environment to manage dependencies:
Code:
python -m venv venv- Activate the virtual environment:
Code:
venv\Scripts\activate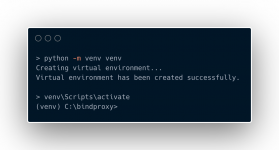
Step 4: Install Required Packages
- While in the virtual environment (you'll see (venv) at the beginning of your command line) install the required packages:
Code:
pip install dnspython PySocks tabulate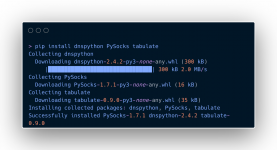
Step 5: Create the Proxy Script
- Create a new file called bindproxy.py in the project directory using any text editor (Notepad, VS Code etc.)
- Copy the full code above into this file and save it
Step 6: Run the Proxy
- In Command Prompt with the virtual environment activated, run:
Code:
python bindproxy.py
Code:
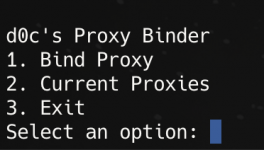
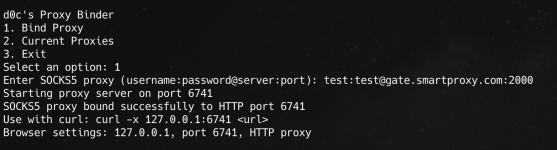
d0c's Proxy Binder
1. Bind Proxy
2. Current Proxies
3. ExitStep 7: Bind a SOCKS5 Proxy
- Select option 1 by typing 1 and pressing Enter
- Enter your SOCKS5proxy details when prompted:
- Format: username: password@server: port
- Example: user123: pass456@gate.smartproxy.io:1080
- The tool will bind this proxy to a random local port between 6700-6900

Step 8: Configure Your Browser to Use the Proxy
- Open your web browser or your antidetect
- Set the HTTP proxy to 127.0.0.1 and the port to the one shown in the tool (e.g. 6708)
- Test the connection by visiting a website
Time to make sure this shit actually works:
- Visit ipinfo.io in your browser - it should show a residential IP from your proxy provider, not your real IP
- Go to DNSLeakTest.com and run a standard test - the results should show Cloudflare DNS (not your ISP or proxy provider) (Ive covered this already but make sure to use a double-barrier approach if you are using a proxy outside of your own country since 1.1.1.1 connects to the nearest CF CDN, not having a VPN will make 1.1.1.1 leak your country)
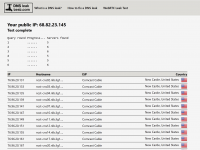
- Head to https://1.1.1.1/help - this Cloudflare diagnostic page will confirm if you're actually using their DNS
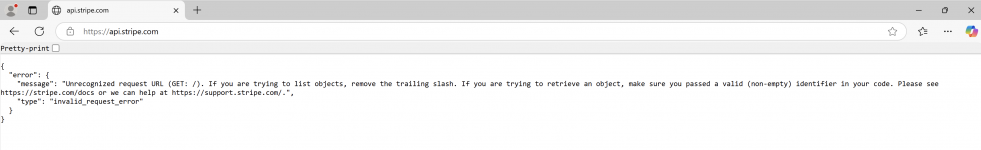
- The moment of truth: navigate to https://api.stripe.com - if it loads instead of timing out congratulations! Youve successfully bypassed the proxy's financial site blocking
Conclusion
This method is the digital equivalent of putting on a disguise and sneaking past the bouncer. Your browser connects to my local proxy script, which handles the DNS resolution through Cloudflares clean 1.1.1.1 servers then forwards everything through your residential proxy.
Why is this better than other methods? Simple - it's transparent as fuck. You can see exactly what the code is doing, modify it if needed and it works with any browser that supports HTTP proxies - no more compatibility headaches.
The proxy providers think youre just accessing random IP addresses, when in reality you're hitting up financial sites without triggering their blocks. It's the perfect solution for carders who need clean IPs that can reliably access payment processors.
Now stop fucking around with broken setups and use a tool built specifically for our needs. d0ctrine out.