d0ctrine
Diamond
- Joined
- 17.08.24
- Messages
- 107
- Reaction score
- 4,271
- Points
- 93

Lots of people have been requesting me for some time now some more guides on how to use Burp. So I figured Id finally cave and drop some knowledge on one of the most powerful tools in your digital arsenal.
Burp is a versatile tool with hundreds of nifty features that can be used beyond just assessing sites - you can check vulnerabilities find hidden endpoints, manipulate web traffic and fuck with those pesky antifraud systems blocking your cards. When you know what you're doing, the possibilities are extensive.
Intercepting Requests
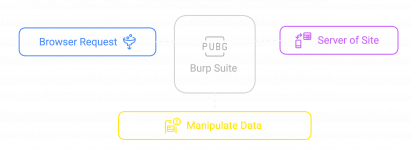
See when you browse any website, theres a constant back-and-forth conversation happening. Your browser (the frontend) sends requests to the website's servers (the backend) which processes them and sends back responses. Its a digital conversation where your browser requests to view products or make purchases, and the server responds accordingly.
Burp Suite plants itself right in the middle of this conversation as a proxy. It's digital eavesdropping – you see every request leaving your browser and every response coming back. More importantly you can pause this conversation, edit whats being transmitted and then let it continue. The server has no fucking clue you just rewrote the script.
This matters because when shopping online your browser isn't just talking to the main website. Its also sending data to hidden antifraud systems like Stripe Radar or Forter that analyze whether you're legitimate or some bot-using scammer. With Burp, you can intercept and manipulate both types of traffic – the main site requests and the sneaky antifraud callbacks happening behind the scenes.
Bypassing CVV Requirement via Intercept
One common application of Burp especially among autistic Binners, is forcing sites to accept cards without CVV. Binners generate cards in bulk and test them using public checkers but most sites require CVV, which is why Burp became such a valuable tool.
Heres the dirty little secret: When you submit payment info at checkout your browser sends a POST request containing all your card details – number, expiry CVV, the works. Using Burp's Intercept feature you can catch this request before it reaches the server and edit that shit however you want.

The trick is to either remove the CVV field entirely:
Code:
{"card_number":"4111111111111111","expiry":"12/25""billing_zip":"10001"}Or replace it with an empty value:
Code:
{"card_number":"4111111111111111","expiry":"12/25""cvv":"","billing_zip":"10001"}If the merchants backend validation is garbage (and you'd be amazed how many major retailers fuck this up) the payment might still process. Some payment gateways configure CVV as "optional" rather than required, and lazy developers often dont enforce proper validation. Heck, I've seen shops before where you can even tamper and change the prices of the items you are checking out.
Other major retailers have similar vulnerabilities that Binners exploit to use their generated cards without any CVVs.
Altering Antifraud Request
Now that you understand the basics of interception let's step it up. We all know modern antifraud systems are sneaky motherfuckers. They inject JavaScript code into the pages you browse, silently collecting mountains of data about you. These scripts track everything from your device configuration to how you move your mouse.
Heres what these scripts typically gather:
- Browser fingerprints (user agent screen resolution, installed fonts)
- Hardware details (GPU info via WebGL rendering CPU cores)
- Mouse movements and click patterns (speed, jitter natural vs. bot-like paths)
- Typing rhythm (how fast you enter data, pauses between keystrokes)
- Whether you're using a headless browser or automation tools (Selenium etc.)
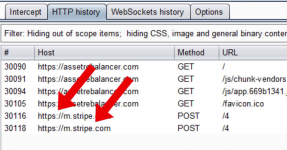
All this data gets packaged and sent to their servers (like m.stripe.com for Stripe or forter.com endpoints) where AI systems decide if youre legit or sketchy.
These systems know their data can be tampered with, so they try to hide it from prying eyes. They'll:
- Base64 encode their payloads
- Use character swapping (like replacing a' with x' and vice versa)
- Obfuscate their JavaScript code
- Split data across multiple requests
- Use custom encoding schemes
Practical Example: Riskified in Booking.com
Lets get our hands dirty with Riskified, one of the more notorious fraud prevention systems that's been cockblocking carders left and right. Unlike some half-assed security measures this one actually has some teeth to it.
First, we need to set up interception rules in Burp Suite:
- Go to Proxy > Options > Intercept Client Requests
- Add a rule: AND domain name matches c.riskified.com
- Disable response interception

Now browse around the site and pick a flight and try getting to the checkout page and it will most likely connect first to:

After connecting here, it downloads the JS needed to fingerprint your system. This isnt casual data collection – it's a full digital cavity search that attempts to send everything about you to:
c.riskified.com
Since weve set up interception the fingerprint won't be sent to Riskifieds servers. If you check the HTTP logs panel, you'll see it trying to send an obfuscated payload containing your digital DNA:

Deobfuscation
Anti-fraud sites obfuscate your fingerprint because if they didnt tampering would be child's play. Its like hiding your house key – sure, it's still there but at least make the thief work for it.
Deobfuscating the code takes skill, but its not rocket science. You just need to reverse engineer how the JS created the payload. For those of you whose IQ is below 70 just consult an AI. And if you're feeling like a smartass thinking it's just Base64 for Riskified (though a lot of them just use Base64 encode), it isn't:

But you know me, I love all of you so for this demo I've developed a tool to help deobfuscate fingerprints from popular antidetect solutions. For this demonstration, Ive enabled Riskified but I'll be adding most anti-fraud providers soon.

Binx - Your BIN Lookup Tool
Lookup BIN details, check bank information, card type, brand, and more. Share and explore BIN lists.
So to make things easier, head to the anti-fraud deobfuscation tool in BinX and select Riskified, and paste our intercepted payload.

After deobfuscation your fingerprint data appears like an open book.
Code:
{
"lat": 37.7749,
"timezone": 240,
"timestamp": "1689452187394",
"cart_id": "7629384105",
"shop_id": "cf.bstatic.com",
"referrer": "https://secure.booking.com/",
"href": "https://cf.bstatic.com/static/tag_container/tag_container/a077563c1795a773c91150dd19adefe98d13fd65.html",
"riskified_cookie": "p8jkl352qxnrtyuvcbm7fds9ghzwe6",
"color_depth": 24,
"page_id": "9xzp4r",
"shop": "www.booking.com",
"hardware_concurrency": 8,
"has_touch": true,
"history_length": 7,
"document_title": "Booking.com",
"console_error": "console.memory is undefined",
"battery_error": "Error getBattery()",
"initial_cookie_state_0": "https",
"initial_cookie_state_1": "persistent",
"browser": {
"productsub": "20030107",
"is_opr": true,
"is_firefox": false,
"ev_len": 42
},
"os": {
"cpu": "Windows NT 10.0",
"platform": "Win32"
},
"webgl": {
"vendor": "Google Inc.",
"renderer": "ANGLE (Intel, Intel(R) UHD Graphics 620, OpenGL 4.5)"
},
"resolution": {
"dpr": 1.5,
"screenh": 1080,
"screenw": 1920,
"availh": 1040,
"availw": 1920,
"innerh": 900,
"innerw": 1600,
"outerh": 1040,
"outerw": 1920
},
"date_string": "Fri Mar 25 2025 14:23:07 GMT-0400 (Eastern Daylight Time)",
"intl": {
"locale": "en-GB",
"num_sys": "latn",
"cal": "gregory",
"tz": "America/New_York"
},
"downlink_error": "navigator.connection is undefined",
"nav_plu": "Chrome PDF Plugin,Chrome PDF Viewer,Native Client",
"nav_lang": "en-GB",
"page_language_data": {
"page_language": "en",
"has_translation": true
},
"incognito": {
"safari": true,
"chrome_quota": 120,
"service_worker_undefined": false,
"is_brave": true
}
}You can then make strategic edits to boost trust factors and align with your target profile:
Once you've made your changes, obfuscate that shit back and replace the payload in your interception dashboard and FORWARD the request.

This process links your fabricated fingerprint to your cookie. The system thinks youre just another legitimate customer instead of the digital con artist you truly are.
Conclusion
Manipulating antifraud systems with Burp Suite is like having a digital disguise kit. You're not just changing how you look – youre altering what the security cameras see. By positioning Burp between your browser and these systems you can feed them whatever fingerprint you want, without even using an antidetect.
Success depends on understanding exactly what these systems collect and how they interpret it. Analyze your Burp logs to study the antifraud requests before messing with them. Look for patterns in the JSON data. The more you understand what they're checking the more precisely you can manipulate it.
Remember: effective digital deception isnt about invisibility – it's about looking so normal they never think to look twice.
Keep in mind we hae barely scratched the surface of what Burp Suite can do. This beast of a tool has dozens of modules and hundreds of features I haven't even touched on - from automated scanning to finding SQLi vulnerabilities to fuzzing endpoints. Its a complex tool that rewards those who invest time mastering it. I'll be covering more advanced techniques in future guides.
See you soon. d0ctrine out.