d0ctrine
Diamond
- Joined
- 17.08.24
- Messages
- 107
- Reaction score
- 4,178
- Points
- 93

You think sharing images online is just harmless fun? That there's no way anyone can trace that shit back to you? Wake the fuck up. The metadata embedded in your photos is a digital fingerprint leading investigators straight to your doorstep. It's literally the first thing any competent investigator checks when trying to unmask anonymous users.
Every digital image you take carries invisible baggage – metadata that records exactly what device you used, when you used it, and often where you were standing when you clicked the shutter.
Your average photo contains three types of metadata tags:
- Exif: Automatically added by your camera/phone – device make/model, exact timestamp, GPS coordinates, camera settings, sometimes even your device's serial number
- IPTC: Usually added by photographers – copyright info, descriptions, keywords
- XMP: Adobe's format – tracks editing history and processing
The FBI and other agencies routinely extract this shit with specialized tools like ExifTool, EnCase, or FTK Imager. One command and they can see every detail about when, where, and how your photo was taken. In court cases, they've specifically cited metadata as "critical evidence" that's "very hard to change" without detection.
Geotagging is by far the most dangerous element. Those innocent vacation pics contain precise GPS coordinates pinpointing exactly where you stood. Exact fucking latitude and longitude. For carders and fraudsters, this is basically drawing a map to your doorstep for law enforcement.
Don't be fooled by social media platforms either. While Telegram, Imgur, and Facebook do strip metadata from public-facing images, the companies themselves retain access to the original files (and metadata) on their servers. One court order and they're handing that shit over to investigators.
Screenshots are somewhat safer than camera photos since they typically don't contain GPS data, but they still embed your device info, screen resolution, operating system, and exact timestamp. Enough to narrow down suspects in many cases.
How To Strip Metadata Manually
Here's how to strip that incriminating metadata and avoid getting caught like a dumbass:
Online Tools (Quick & Easy)
- VerExif or Metadata2Go or Jimp: Upload image, click "remove metadata," download clean version
- But remember – you're trusting a third party with your potentially sensitive file
- Windows: Built-in (Properties → Details → "Remove Properties"), FileMind QuickFix (drag & drop), EXIF Purge (batch processing)
- Mac: ImageOptim (free, drag & drop), Exif Metadata (native app), Preview export (limited)
- Linux: ExifTool, ImageMagick, GIMP (with export options)
- Android: Photo Metadata Remover, ExifEraser (privacy-focused), Photo Exif Editor
- iOS: Metapho, Exif Metadata, Photo & Video Metadata Remover
Command Line (The Proper Way)
- ExifTool: exiftool -all= image.jpg nukes ALL metadata
- ImageMagick: mogrify -strip image.jpg removes most metadata
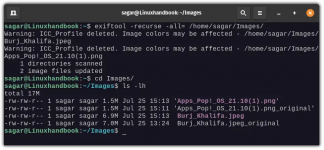
Always verify your metadata is actually gone by checking the file again before sharing. Many tools claim to clean metadata but leave traces behind.
Outside of OPSEC
Metadata isn't just an OPSEC concern – it has legitimate uses in verification systems that you need to be aware of:
When submitting documents to places like Amazon or financial institutions, their automated systems often check metadata to verify authenticity. They're looking for:
- Timestamps matching claimed dates
- Image source (camera vs. screenshots vs. Photoshop)
- Signs of manipulation in the editing history
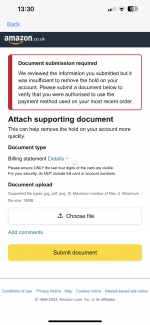
If you're trying to get a transaction approved with documentation, metadata inconsistencies can trigger automatic rejection. For instance, if your receipt shows March 2023 but the photo metadata says it was created in 2022, that's an instant fraud flag. Verification systems check for these discrepancies automatically.
Caught Retards
Think I'm exaggerating about metadata risks? History is littered with the digital corpses of people who thought they were too smart to get caught by something as simple as image data.
These aren't hypothetical scenarios—these are real-world fuckups that sent people to prison or blew their cover because they couldn't be bothered to spend 30 seconds cleaning their metadata:
John McAfee: I love this motherfucker. This legend turned international fugitive was hiding from murder charges in 2012 when a Vice reporter posted a photo with him. The genius reporter forgot to strip the EXIF data, which contained precise GPS coordinates pointing to Guatemala. Local authorities arrested McAfee within hours. A fucking tech legend caught because of one metadata mistake.


Higinio Ochoa (w0rmer): This Anonymous-affiliated hacker broke into multiple police databases in 2012. To taunt authorities, he posted a photo of his girlfriend holding a sign saying "PwNd by w0rmer & CabinCr3w." Problem was, he didn't strip the EXIF data. The iPhone photo contained GPS coordinates leading to Wantirna South, Australia – his girlfriend's home. FBI extracted these coordinates, cross-referenced his Facebook, and arrested him in Texas. He got 27 months in federal prison.
Dark Web Drug Dealers: In 2016, two Harvard researchers analyzed 223,000 images from darknet marketplaces and found 229 photos with intact GPS coordinates. These coordinates mapped directly to dealers' homes or stash houses. Despite operating on "anonymous" Tor networks, these idiots were broadcasting their physical locations through their product photos.

Conclusion
Every image you share is potentially a digital snitch carrying more identifying information than your driver's license. One careless upload can undo months of careful OPSEC and lead investigators straight to your doorstep.
The solution is simple but critical: strip ALL metadata before sharing ANY image. It takes seconds to do but can save you years behind bars. Don't be the next dumbass in a criminal case where the prosecutor's star witness is a JPEG file.
For carders and fraudsters especially, image metadata hygiene isn't optional – it's survival. Assume every image is trying to get you caught unless you've personally verified it's clean. In the digital underground, paranoia isn't a mental disorder – it's a fucking life skill. d0ctrine out.