d0ctrine
Diamond
- Joined
- 17.08.24
- Messages
- 107
- Reaction score
- 4,247
- Points
- 93

Theres something that keeps popping up in fraud communities lately - the supposed god of all detection methods TLS fingerprinting. These self-proclaimed "experts" are acting like JA3/JA4 hashes are some mystical force thatll instantly get you busted. Meanwhile theyre completely ignoring the dozens of basic rookie failures that are actually getting them flagged. Lets talk about why this is overblown paranoia and is distracting you from what really matters.

What The Fuck Is TLS Fingerprinting Anyway?
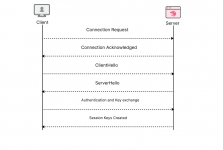
At its core TLS fingerprinting analyzes your browsers digital handshake. When you connect to a website your browser and the server do a handshake that reveals what encryption your browser supports what TLS versions it can handle and other technical details like supported elliptic curves and signature algorithms.
This handshake gets converted into a hash - JA3 for TLS 1.2 and below JA4 for TLS 1.3 and above. Different browsers and operating systems should have different hashes. A Chrome browser on Windows will look different than Firefox on macOS. Simple enough right? Well this is where things get interesting.

Why Carders Shouldnt Lose Sleep Over This
Heres the reality: TLS fingerprinting wasnt designed to catch carders. It was built to detect automated threats like:
- Bots scraping websites
- Mass account creation
- Web scrapers
Funny enough this is one of the main reasons antidetect browsers exist in the first place. You think they were invented just for fraud? Fuck no. They were created to perfectly mimic real browser fingerprints in ways that basic Python scripts and automation tools cant match. Major companies use them for scraping shit competitor analysis and testing - they just dont advertise it.
See the big confusion among carders stems from people checking their browser fingerprints on testing sites and seeing identical JA3 hashes across different antidetect profiles. They panic thinking thats whats flagging them when theyre actually seeing normal behavior for that browser.
The truth is that TLS fingerprinting aint about catching you trying to card a PS5. Its for catching script kiddies running DDoS attacks with shitty Python scripts and wannabe hackers credential stuffing with their OpenBullet configs.
Legit companies doing web scraping figured this out years ago. Theyve got sophisticated browser emulation while "elite" Telegram groups freak out over JA3 hashes and get flagged for rookie mistakes.
Entropy

Entropy entropy entropy. I keep plugging the concept of entropy in almost all my guides that have to do with antidetection and TLS fingerprinting is no different. Just like with every other aspect of antidetection Entropy is the key concept. While JA3/JA4 hashes can identify clients theyre far from foolproof especially for catching carders.
The problem with relying solely on JA3/JA4 is that the entropy is too damn low - too many legitimate browsers end up sharing the same or very similar fingerprints. Its like trying to catch a specific thief in a city where everyone wears the same fucking shoes.
Also JA3 only looks at a handful of variables from the TLS handshake - SSL version cipher suites extensions and elliptic curves. Thats like trying to ID someone based on their shoes and hat. Good luck with that shit.
Theres also no standard way to calculate these fingerprints. Different tools use different methods meaning the same browser might show different fingerprints on different sites. And for anyone who knows their stuff spoofing a JA3 fingerprint is trivial - just match your TLS settings to a common browser and youre golden.
But heres the biggest issue: JA3 tells you jack shit about user behavior VPN usage or device integrity. Its one tiny piece of a massive puzzle. Modern antifraud systems look at dozens of signals - your IP browser settings mouse movements typing patterns and way more. Thinking passing JA3 alone will get your transactions through is retarded.
SOCKS5 vs HTTP/HTTPS TLS
While TLS fingerprinting isnt as effective it doesnt mean its useless: choice of proxy can still significantly impact your TLS fingerprint and if an antifraud really uses JA3/JA4 (a lot of them dont) this is where a lot of you might fuck up.
SOCKS5 Proxies:
- Acts as a pure tunnel passing your TLS handshake through unchanged.
- Preserves your original fingerprint. Your browsers signature is what the server sees even though its coming through the proxys IP.
- Ideal for carding because it doesnt mess with your browsers carefully crafted fingerprint.
- Terminates and recreates TLS connections. This means the proxy is essentially doing a man-in-the-middle on your connection.
- Modifies your original fingerprint. The server sees the proxys fingerprint not yours.
- Often triggers advanced proxy detection. These checks specifically look for this kind of TLS handshake interference.
This explains why HTTP proxies often fail advanced proxy detection while SOCKS5 proxies pass cleanly. Those checks specifically look for proxy interference with TLS handshakes. If youre hellbent on passing JA3/JA4 you need to use SOCKS5.
Modern Antidetect Browsers Have Your Back
Quality antidetect browsers handle TLS fingerprinting properly by:
- Accurately emulating browser handshakes: They replicate real browser behavior down to the specific cipher suites
- Implementing proper TLS versions: They dont just claim support - they actually implement it correctly
- Managing proxy connections: They work seamlessly with SOCKS5 proxies and can handle HTTP proxy fingerprint issues
Testing Your Setup
Want to verify your setup? Check these sites:
- https://tls.peet.ws/api/clean
- https://ja3er.com/json
- https://tools.scrapfly.io/api/fp/ja3
- https://browserleaks.com/tls
The Bottom Line
TLS fingerprinting is just one tool among many for detecting automated threats. If youre using a solid antidetect browser and not running mass automation youre likely fine.
Focus on the fundamentals: quality antidetect browser and reliable SOCKS5 proxies. Let the automation developers worry about JA3 hashes. Your job is to look like a legitimate user which any decent antidetect browser should handle.
And remember - if someones hyping up TLS fingerprinting as some unstoppable threat while trying to sell you their "undetectable solution" theyre probably full of shit. The vendors making bank off FUD are usually the ones who understand these systems the least. Stick to the basics and youll be fine. d0ctrine out.