A new Python-based information stealer targets sensitive data from European and Asian organizations.
A Vietnamese-speaking threat actor has deployed a new Python-based malware called PXA Stealer in a campaign targeting government and education entities across Europe and Asia, according to research from Cisco Talos.
The malware is designed to extract sensitive data including:
- Online credentials
- VPN and FTP client information
- Financial records
- Browser cookies
- Gaming software data
Technical analysis links the operation to Vietnam through Vietnamese language comments in the code and a Telegram account named "Lone None" containing Vietnam's national flag and Ministry of Public Security emblems. The threat actor was observed selling Facebook and Zalo credentials along with SIM cards in Telegram channels previously connected to another Vietnamese group called CoralRaider.
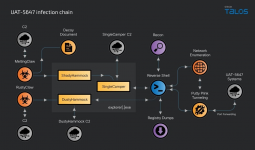
The attack chain begins with phishing emails containing ZIP attachments that deploy a Rust-based loader and Windows batch scripts. These execute a decoy PDF while downloading additional payloads to disable antivirus protection and install the stealer. PXA Stealer specifically targets Facebook business accounts to gather advertising and account data through Facebook's Ads Manager and Graph API.
The discovery comes amid rising concerns over information-stealing malware, with researchers tracking multiple new variants like Amnesia Stealer and Glove Stealer, as well as updates to existing families such as RECORDSTEALER and Rhadamanthys. IBM X-Force recently identified another campaign by initial access broker Hive0145 using StrelaStealer to target European organizations since April 2023.