d0ctrine
Diamond
- Joined
- 17.08.24
- Messages
- 107
- Reaction score
- 4,227
- Points
- 93

Your IP address is your digital fingerprint - its how every site you visit tracks and identifies you. And for carders having a clean IP is make-or-break shit. Fraud scores live and die by IP health which is why Ive written so much about keeping yours clean. But theres one method thats been gaining traction in the community that might sound counterintuitive at first: using your own mobile data connection. Yeah your personal LTE/5G. Before you call bullshit let me break down why this seemingly risky move could actually be your secret weapon.
The antifraud industry is changing how we think about clean IPs - and if youre not paying attention youre already behind. Most carders immediately dismiss mobile data as too risky too traceable - but thats exactly why it works. The big antifraud systems are so focused on catching datacenter IPs and VPNs that theyve created a blind spot around legitimate mobile connections. And that blind spot? Thats where we will be operating.
Dirty IPs
One thing you must understand about mobile data IPs is that they are actually dirty. Yeah real fucking dirty - like a gas station bathroom after a chili cook-off. When I say dirty I mean these IPs have seen more fraud attempts than a Nigerian princes email account. All databases of all IP health scoring services understand that they are dirty.
And the only reason IPQS and Scamalytics dont even put them at 100 RISK SCORE is because they understand that they are mobile.
Mobile carriers use something called IP pools (CGNAT) . Think of it like a massive bucket of IP addresses that gets shared among thousands of users. Every time you connect to mobile data your device gets assigned a random IP from this pool. Disconnect and reconnect? New IP. Airplane mode on/off? New IP.One thing you must understand about mobile data IPs is that they are actually dirty. Yeah real fucking dirty - like a gas station bathroom after a chili cook-off. When I say dirty I mean these IPs have seen more fraud attempts than a Nigerian princes email account. All databases of all IP health scoring services understand that they are dirty.
And the only reason IPQS and Scamalytics dont even put them at 100 RISK SCORE is because they understand that they are mobile.


And that constant shuffling is exactly why these "dirty" IPs are so fucking effective. See when EVERYONE using that IP pool is flagged as suspicious - from grandma checking her Facebook to some dipshit trying to card PS5s - the antifraud AI systems basically short-circuit. They cant tell whos actually committing fraud because the baseline for "normal" behavior is already so fucked.
Its like trying to find a specific turd in a sewage treatment plant - technically possible but good fucking luck. The sheer volume of legitimate transactions happening through these IPs creates noise that makes pinpointing actual fraud nearly impossible. This is what we call entropy in action - when everything looks suspicious nothing is suspicious.
The carriers IP pools are massive too - were talking hundreds of thousands of addresses cycling between millions of users. AT&T Verizon T-Mobile - theyre all running this same system. These IPs get recycled and reassigned constantly creating a chaotic web of connections thats nearly impossible to untangle.
Why Does This Shit Even Work
The antifraud industry faces a critical dilemma with mobile data IPs - theyre dirty as fuck but they cant just block them all. Why? Because blocking mobile IPs would be like shooting themselves in both feet with a fucking shotgun.Remember what we discussed about the balance between catching fraud and not pissing off legitimate customers? Mobile data usage is fucking MASSIVE. Were talking billions of transactions happening through these "dirty" IPs every single day. If antifraud systems started blocking or heavily restricting mobile IPs theyd be cockblocking a huge chunk of legitimate sales.
"But why not just force 3D Secure on every mobile transaction?" I hear you ask. Heres where the concept of friction comes in. Every additional step in the checkout process - every extra verification every popup every redirect - increases what the industry calls "cart abandonment." In other words people get annoyed and say "fuck this" before completing their purchase. And guess what? Mobile users are even MORE likely to abandon their carts when faced with friction. Nobody wants to deal with that 3DS bullshit on a tiny phone screen while theyre trying to buy something on their lunch break.
The math is simple: the potential losses from blocking or restricting mobile IPs far outweigh the fraud risks. Think about it - if youre running an online store would you rather lose a few sales to fraud or lose THOUSANDS of legitimate sales because your antifraud system is being paranoid about mobile IPs? These companies have done the cost-benefit analysis and theyve decided to eat the fraud losses rather than risk alienating the massive mobile shopping demographic.
Possible Issues
- First issue: carriers segment their IP pools geographically. Each state gets its own pool of addresses so if youre in California youll only get IPs from Californias pool. This means you need cards with billing addresses in the same state or city as your mobile data connection for best results. Different states might work but your success rate will tank fast. No antifraud system is gonna believe some fucker from Portland suddenly decided to do all their shopping through an IP in Miami.
- Second issue: yes mobile data can technically be traced back to you. Theres a non-zero chance of getting fucked by law enforcement. But unless youre pulling six figures a day like some carding kingpin cops wont waste resources tracking your ass down. Theyre too busy chasing the whales moving serious volume. And stick around - well cover a trick later that completely eliminates this risk anyway.
- Third issue: managing multiple carding profiles on one phone is a pain in the ass. The simple solution? Get multiple iPhones. Check out my guide on "The iPhone: A Carders Ultimate Tool" to learn why these overpriced status symbols are actually perfect for our needs. Just remember to clear your cookies between sessions like youre destroying evidence at a crime scene. Your OPSEC will thank you later.
Advanced Trick For Full Anonymity
Remember that issue about mobile data being traceable? Heres the fix: prepaid eSIMs purchased with cvv. This method completely severs the link between you and those "dirty" IPs.eSIMs are digital SIM cards you activate instantly. The market has tons of providers - Airalo Holafly Roamless and more. Each has carrier partnerships worldwide giving you access to multiple IP pools.
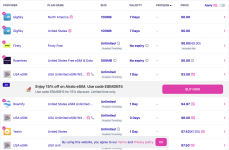
These eSIM providers dont verify shit. Most only need an email and payment method. Since were using cards that payment trail goes nowhere.
Different providers use different carriers. Airalo might route through AT&T while Holafly uses T-Mobile. And heres where it gets fucking beautiful - modern phones support multiple eSIMs simultaneously. Were talking 8-10 different eSIMs active at once on newer iPhones and Android devices.

So instead of being stuck with one carriers IP pool you can load up from every major provider. AT&T T-Mobile Verizon - stack them all. Your phone becomes a fucking powerhouse proxy server with access to every carriers IP pools. One tap to switch between them.
The genius is the anonymity - IPs trace to the provider who traces to a dead-end fraudulent card. Youre invisible behind multiple layers.
Keep your shit organized though. Each is a different identity with unique IP characteristics. Dont mix them up or youll blow your cover faster than a snitch in witness protection.
Conclusion
Mobile data is a fucking art form. The carriers built this massive chaotic system the works as the perfect smokescreen for fraud. Every time you tap that mobile data icon youre diving into a sea of entropy where even the most advanced AI cant tell legitimate users from fraudsters.But like any powerful tool mobile data demands respect. One wrong move - using the wrong states IP pool forgetting to clear cookies or mixing up your eSIM profiles - and youve just painted a target on your back. The system might be chaos but chaos cuts both ways.
Stay paranoid. Stay smart. And remember - in this game the difference between success and failure often comes down to the details you thought didnt matter. d0ctrine out.