Fixxx
Moder
- Joined
- 20.08.24
- Messages
- 1,060
- Reaction score
- 4,088
- Points
- 113
"Confirm that you are not a robot": A new wave of cyberattacks using fake CAPTCHA tests.
Kaspersky Lab has detected a new wave of attacks using fake CAPTCHAs - tests designed to distinguish humans from bots, as well as error messages in browsers styled to look like Google Chrome. Initially, a PC user clicks on a semi-transparent ad banner on a website, which is subtly stretched across the entire screen. They are then redirected to a malicious page where they are asked to perform several steps supposedly to verify protection against bots or to fix a browser issue. As a result of following the "instructions", a stealer (malware designed to steal data) is downloaded onto the user's computer. The majority of such attacks have been found in Russia, Brazil, Spain and Italy.
The scheme is old - the tools are new.
Earlier this year, similar cyberattacks using the Lumma stealer were reported. At that time, the main target of the attackers was gamers: malicious ad banners were displayed on sites with pirated games. Now the malware is spreading through other means, such as betting sites, adult content resource and anime communities.
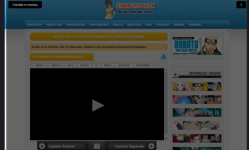
*An example of a site that redirects the user to a captcha.
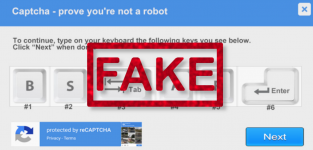
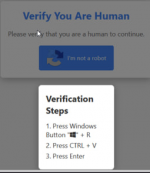
In addition, attackers have started using not only the Lumma stealer but also the Amadey Trojan. Like Lumma, it allows for the theft of usernames and passwords from browsers and cryptocurrency wallets, as well as performing other actions, such as taking screenshots or downloading remote access tools to the victim's device, giving attackers full control over the device. The infection process occurs as follows: the user must follow several steps according to the instructions, such as pressing specific key combinations in sequence. As a result, a malicious PowerShell script is launched on the device, which downloads the malware.
*Captcha with instructions.
Once the user's data is obtained, the malware also begins to actively "visit" various advertising addresses: likely, this is how the attackers gain additional profit by inflating views from the infected device, similar to adware. Buying ad space for banners that lead users to malicious pages is a common method among attackers. However, in this campaign they have significantly expanded their reach by placing malicious ads on websites of various themes and also used a new script with fake browser errors. This serves as a reminder that attackers are constantly evolving and improving their methods. To avoid falling for their tricks, companies and users are advised to critically assess any suspicious information they encounter online.