d0ctrine
Diamond
- Joined
- 17.08.24
- Messages
- 107
- Reaction score
- 4,257
- Points
- 93

Our iPhone guide showed how mobile devices are goldmines for carding - they blend in seamlessly with normal traffic and slip past antifraud like a ghost. But what if youre broke as fuck or just hate Apples overpriced bullshit? Dont worry theres another option thats been gaining serious traction: mobile antidetects. These services are revolutionizing the game by giving you access to real physical devices without dropping thousands on hardware. And unlike traditional antidetects that just pretend to be phones this shit actually works because youre controlling genuine mobile devices remotely.
Lets be crystal clear about what were discussing here because theres a lot of bullshit floating around about mobile antidetects. First lets eliminate what were NOT talking about:
- Mobile browsers with built-in antidetect features (like "private" or "mimic" modes) - This is unreliable garbage that still leaks your real device info through WebRTC canvas fingerprinting and sensor data.
- Traditional antidetects like AdsPower Dolphin or GoLogin pretending to be phones - Pure garbage that gets flagged instantly. Their mobile emulation is a joke - wrong screen ratios broken sensors and fingerprints that gets flagged by half-decent antifraud system.
- Android emulators with spoofing tools - Dont even get me started on this. If youre using Nox or BlueStacks for work you deserve to get caught.
The major players in this space are:
- Geelark - Popular cloud phone service that excels at running native mobile apps. Browser fingerprints are less unique so focus on app-based operations.
- MoreLogin Cloud Phone - Similar to Geelark with native app support. Both services share browser fingerprints making app usage the optimal approach.
- AWS Device Farm - Enterprise-grade device cloud with extensive app testing capabilities. Requires technical expertise but offers unmatched device variety.
- Browser Stacks Real Device Cloud - Another enterprise solution focused on app testing. Complex setup but provides genuine device access for native applications.

Critical warning: I've run extensive test with both GeeLark and Cloud Phone and they share canvas fingerprints making them potentially detectable. Do not use their browsers to card. The real power of these services lies in running native mobile apps - thats where you get the benefits. If you plan to use them just for the browser an iPhone remains your best bet. But for these services use them for carding in-app.
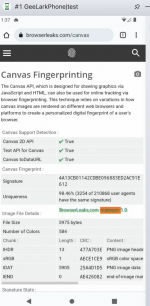
How Are They Effective?
Think about why iPhones work so well as we discussed previously - they blend in perfectly with normal traffic. Mobile antidetects operate on the exact same principle. When youre remotely controlling a popular phone configuration (using app instead of browser) you become just another face in the crowd - completely indistinguishable from thousands of regular users. The antifraud systems cant flag you because your device signature matches what they expect to see from legitimate customers.
The real magic happens with native apps. While PayPal Cash App banking sites and booking sites have transformed their websites into impenetrable fortresses with advanced fingerprinting that makes browser antidetects obsolete their mobile apps remain far more vulnerable. The native app environment simply doesnt have the same level of sophisticated detection.
Since youre not touching the browser at all you completely sidestep the fingerprinting arms race. Traditional antidetects can spoof all they want but theyll never match real hardware. Cloud phones give you legitimacy because youre controlling genuine physical devices and sticking to native apps - no browser fingerprinting to worry about.

When you fire up a mobile antidetect youre getting direct access to install and run apps exactly like a normal phone. No more wrestling with browser detection - youre using the apps exactly as they were designed to be used. Your device looks legitimate because it actually is legitimate hardware making it virtually impossible for apps to distinguish between your session and any other users phone.
Best Practices
Lets talk device selection. For GeeLark and Cloud Phone just pick the most updated configuration - they manage the device specs for optimal performance. On AWS farm the Samsungs and Popular Chinese Phones are perfect - they disappear into the crowd of normal users. Some obscure nobody-uses phones like Xperia or LG? Wont work for long as you will be correlated sooner or later.
Your OS version needs to match what regular people are running. Most users update their phones pretty quickly these days but theres always a sweet spot - about 2-3 months behind the latest release. Thats where you want to be to perfectly blend in.
Now for a mistake I see constantly: fucking with system settings. Every time you toggle some obscure Android setting or tweak a system parameter youre making your device stick out like a sore thumb. Default is beautiful. Default is safe. The more your setup looks like it came straight out of the box the better.
Your proxy setup has to make sense too. The whole point of using mobile antidetects is looking legitimate so dont ruin it with mismatched data. Always use MOBILE PROXIES. If your IP says youre in Nebraska but your carrier info shows T-Mobile Miami youve just wasted all that effort on device authenticity.
Lastly heres what makes these services truly powerful - they run on per-minute billing. This means you can treat devices like burner phones switching them out constantly. Orders getting cancelled left and right? Generate a new one. Something feels off? Switch it up. Fresh devices mean fresh fingerprints and that constant rotation keeps you one step ahead.
Mobile Antidetects: Not Quite There Yet
Lets be real - mobile antidetects show promise but theyre not the shit yet. While running real hardware with native apps is a step forward from browser-based bullshit they still cant match the reliability of a properly configured iPhone especially when it comes to using the browser to card stuff.
The technology itself is solid - spinning up fresh devices on demand and running native apps does give you legitimacy. But dont get caught up in the hype. Browser operations are still sketchy as fuck with shared fingerprints and youre limited to specific apps that work well with these services.
For now keep your iPhone as your primary and use mobile antidetects as a supplementary tool where they make sense - specific apps testing configurations or when you need quick rotation. And remember - even with real hardware being sloppy with OPSEC will still get you burned. Match those proxies stick to stock settings and stay paranoid. The antifraud game never sleeps. d0ctrine out.
Last edited: