d0ctrine
Diamond
- Joined
- 17.08.24
- Messages
- 107
- Reaction score
- 4,227
- Points
- 93

Real call spoofing requires serious infrastructure and technical knowledge - not that TextNow app bullshit or Telegram ripper garbage that floods your DMs. Those dipshits selling "private number" services wouldnt know proper spoofing if it slapped them in their face.

This guide breaks down call spoofing from basic concepts to advanced exploitation. No flashy promises, no magic apps - just the hard technical knowledge that lets you bypass modern call detection systems.
Big Money Still Flows Through Voice
Phone systems still drive billions in sales across major retailers. Companies like Victorias Secret, Nordstrom and countless others actively push customers to order by phone. Why? Because old people are retarded when it comes to technology. As to why your granma needs Victoria Secret lingerie, thats a mystery for another day.
But even without direct phone carding, voice spoofing unlocks a trove of opportunities:
- Balance checking at scale
- Mass OTP interception
- Bank account takeover
- Order rerouting/address changes
- Refund fraud at scale
- Corporate account compromise
- Customer service social engineering
The Technical Stack

Modern phone systems are a beautiful clusterfuck of old and new tech mashed together. Understanding this mess matters because most fraud prevention still relies on legacy systems that barely changed since the 90s.
Three levels of spoofing exist in this ecosystem:
- Basic ID Spoofing: What those garbage apps do. Just changes the displayed number without touching underlying call data. Fine for pranking your friends, useless for anything serious.
- Carrier-Level Spoofing: Routes calls through legitimate telcos, making them appear as normal PSTN traffic. Expensive as fuck but nearly impossible to detect. Required for serious bank operations.
- Full SIP Spoofing: The sweet spot for most carders. Controls the entire call chain and mimics legitimate traffic patterns. Needs proper infrastructure but can bypass most detection systems.
Three main types of phone systems matter for us:
PSTN (Public Switched Telephone Network)
The granddaddy of them all. This traditional phone network still connects landlines worldwide. Banks, credit card companies and big corporations use PSTN because its reliable as fuck. When you call Chase or Amex, youre probably hitting their PSTN lines.
For carders, PSTN matters because:
- Most financial institutions trust PSTN calls more than VoIP
- Caller ID spoofing detection barely exists
- Crystal clear audio quality (crucial for social engineering)
- Less recording/monitoring compared to VoIP
Voice transmitted over internet protocol - basically turning voice into data packets. Think Skype or your sketchy calling app. Most modern business phone systems use VoIP because its cheap and flexible.
VoIP advantages for fraud:
- Easy to mask origin location
- Dirt cheap international calls
- Simple operation scaling
- Multiple numbers on one system
- Advanced call routing options
The protocol that makes VoIP work. SIP handles all the setup, teardown and control of VoIP calls. Think of it like HTTP but for voice communication. Most importantly, SIP lets us build our own private phone infrastructure.
Why SIP rocks for carders:
- Complete control over caller ID presentation
- Route calls through multiple servers
- Mix with VPNs for extra anonymity
- Build private phone networks
- No central provider to snitch
Typical call flow looks like this:

Code:
Your Device -> SIP Server -> VoIP Provider -> PSTN Gateway -> Target PhoneEach hop in this chain affects how receiving systems see your calls. Banks dont just check the phone number - they analyze the entire call signature as it passes through this infrastructure.
This is why running your own SIP setup matters. Those "private number" services might work for pizza orders but anything touching financial systems needs proper infrastructure.
The Reality of Caller ID
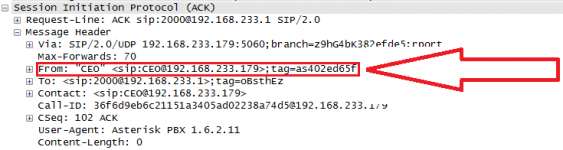
Banks and financial institutions validate incoming calls through multiple layers of checks that cheap spoofers cant bypass. When a call hits their system, they check:
- The presented caller ID number
- Where the call originated from
- Which carriers handled the routing
- Call signaling patterns and metadata
- Historical usage patterns
With SIP you control the entire call chain. Your calls can mimic legitimate PSTN traffic passing through trusted carriers. The secret lies in understanding how different financial institutions validate incoming numbers.
Some banks only check basic caller ID. These are your easy targets - basic number spoofing works fine. Others dig deeper, looking at call routing and carrier signatures. These need proper SIP infrastructure to appear legitimate.
The most sophisticated systems analyze call patterns over time. They track how often numbers hit their system, which carriers route them, and typical usage patterns.
Building Your Own Setup
Here are two methods that actually work without needing a PhD in telecommunications:
Method 1: Carded SIP Trunk
Easiest method that still gets results. Card Twilio, Telnyx or voip.ms. These work fine for most sites.
Requirements:
- Clean card with solid antidetect setup
- Business email (not free email)
- MicroSIP (free softphone)
- Residential proxy
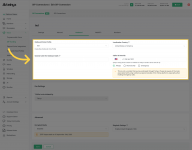
- Card a Telnyx Account (or other SIP providers):
- Sign up for an account with Telnyx or your preferred SIP provider.
- Buy a DID Number:
- Purchase a DID number that matches your target area for local calls.
- Grab Credentials from the Dashboard:
- Log in to your Telnyx dashboard and navigate to the section where you can find your SIP credentials (username, password, and SIP server details).
- Change the Caller ID:
- In your Telnyx account, look for the option to set a Caller ID Override. This allows you to specify the caller ID you want to display when making outbound calls.
- Configure MicroSIP:
- Open MicroSIP and go to Account > Add to create a new SIP account.
- Enter the following details:
- Domain:
(or the SIP server address provided by your provider).Code:
sip.telnyx.com - Username: Your SIP username from the Telnyx dashboard.
- Password: Your SIP password from the Telnyx dashboard.
- Transport: Select TCP.
- Set Local Number as Your DID: Enter your purchased DID number in the appropriate field.
- Domain:
- Save the Configuration:
- Click OK to save the account settings in MicroSIP.
- Test the Setup:
- Make an outbound call using MicroSIP to ensure that the caller ID is displayed as specified and that the call connects successfully.
Method 2: DIY FreePBX
More setup work but better for bank related fraud. Harder to detect since you control the whole system.
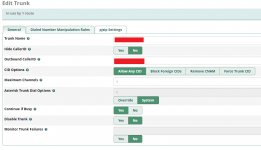
Requirements:
- Carded VPS (OVH or DigitalOcean work fine)
- FreePBX ISO
- DID number from any provider (some are more accomodating to spoofing, so do your own research)
- MicroSIP
- Same proxy setup as Method 1
- Card a VPS:
- Choose a VPS provider and set up your server.
- Download and Install FreePBX:
- Follow the installation instructions for FreePBX on your VPS.
- Basic Configuration in Admin Panel:
- Add Extensions:
- Go to Applications > Extensions and create the necessary extensions.
- Set Outbound Routes:
- Navigate to Connectivity > Outbound Routes and configure your outbound routes.
- In the outbound route settings, find the CID Options to set the default caller ID you want to use for outbound calls.
- Configure Your DIDs:
- Go to Connectivity > Inbound Routes and set up any Direct Inward Dialing (DID) numbers you have.
- Add Extensions:
- Set Caller ID Spoofing:
- In the Outbound Routes, specify the caller ID you want to use in the Caller ID field (make sure you have the right to use this number).
- Ensure your trunk settings allow for caller ID manipulation.
- Point MicroSIP to Your VPS IP:
- Download and install MicroSIP on your local machine.
- Open MicroSIP and go to Account > Add to create a new SIP account.
- Enter the following:
- Display Name: Name for the account.
- SIP Server: Your VPSs IP address or domain name.
- SIP Username: The extension number you created.
- SIP Password: The password associated with that extension.
- STUN Server (optional): Use a STUN server if needed for NAT.
- Save the Configuration in MicroSIP:
- Click OK to save the account settings.
- Test the Connection:
- Make a test call to ensure that the spoofed caller ID is displayed correctly and that the call goes through successfully.
Running your own PBX server will give you more consistency, since these SIP providers are iffy and tend to disable accounts they suspect of malicious activities from time to time. However, if youre just starting, stick with Method 1. Its simpler and good enough for most shit. Only bother with FreePBX if youre doing heavy bank fraud or need total control over your infrastructure.
Conclusion
Call spoofing isn't some magic trick - it's a technical skill that requires serious know-how and infrastructure. If you're still thinking about using some bullshit app or Telegram service, you're missing the point entirely.
Understanding the tech stack is crucial, and DIY setups give you more control and consistency. This guide isn't for wannabes or script kiddies. It's for those ready to put in the work and be better at fraud.
Master these techniques, and you'll open doors that most "carders" can only dream about. Just don't come crying when you fuck up and get caught. This shit's not a game. Stay sharp, stay cautious, and always be learning. The phone system's a mess, and that's your advantage - if you're smart enough to use it. d0ctrine out.


