Introduction
In a significant development for cybersecurity, three individuals in the United Kingdom have pleaded guilty to operating a service that aided criminals in intercepting one-time passcodes (OTPs). This case sheds light on the ongoing battle against online fraud and the sophisticated methods employed by cybercriminals.
The OTP Agency Scam
What was OTP Agency?
OTP Agency, launched in November 2019, was an online service designed to help attackers intercept one-time passcodes. These codes are often used by websites as a second authentication factor, adding an extra layer of security beyond passwords.
How did it work?
The service operated as follows:
The Perpetrators
Three men have pleaded guilty to running OTP Agency:
The Downfall
Initial Exposure
In February 2021, a cybersecurity publication profiled OTP Agency, leading to a panic among the operators. Messages exchanged between Picari and Vijayanathan revealed their concern:
Attempted Revival and Final Shutdown
Despite initially shutting down their website and Telegram channel, OTP Agency attempted to revive their operations just days later. However, this revival was short-lived. The National Crime Agency (NCA) took the site offline less than a month later when the trio were arrested.
The Impact
According to NCA investigators, more than 12,500 people were targeted by OTP Agency users during the 18 months the service was active. The case highlights the ongoing threat of sophisticated phishing and fraud schemes.
Conclusion
The OTP Agency case serves as a cautionary tale for those involved in cybercriminal activities. While this particular service has been shut down, it demonstrates the potential profitability and risks associated with operating such platforms. The case highlights the importance of operational security and the need for constant adaptation in the face of law enforcement scrutiny.
Lessons for Cybercriminals
For those considering similar ventures:
The cybercriminal landscape is constantly evolving, with law enforcement agencies becoming increasingly sophisticated in their tracking and prosecution methods. While new opportunities for illicit gains may arise, the risks of detection and severe legal consequences continue to grow.
Remember, engaging in cybercrime carries serious legal and personal risks. The allure of quick profits must be weighed against the potential for long-term imprisonment and the destruction of one's future prospects.
In a significant development for cybersecurity, three individuals in the United Kingdom have pleaded guilty to operating a service that aided criminals in intercepting one-time passcodes (OTPs). This case sheds light on the ongoing battle against online fraud and the sophisticated methods employed by cybercriminals.
The OTP Agency Scam
What was OTP Agency?
OTP Agency, launched in November 2019, was an online service designed to help attackers intercept one-time passcodes. These codes are often used by websites as a second authentication factor, adding an extra layer of security beyond passwords.
How did it work?
The service operated as follows:
- Scammers who had stolen someone's bank account credentials would enter the target's phone number and name into the OTP Agency system.
- The service would then initiate an automated phone call to the target, warning them about supposed unauthorized activity on their account.
- The call would prompt the target to enter a one-time passcode sent to them via SMS.
- Any codes shared by the target were then relayed to the scammer's user panel on the OTP Agency website.
The Perpetrators
Three men have pleaded guilty to running OTP Agency:
- Callum Picari, 22, from Hornchurch, Essex
- Vijayasidhurshan Vijayanathan, 21, from Aylesbury, Buckinghamshire
- Aza Siddeeque, 19, from Milton Keynes, Buckinghamshire
The Downfall
Initial Exposure
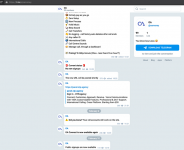
In February 2021, a cybersecurity publication profiled OTP Agency, leading to a panic among the operators. Messages exchanged between Picari and Vijayanathan revealed their concern:
Picari: "bro we are in big trouble… U will get me bagged… Bro delete the chat"
Vijayanathan: "Are you sure"
Picari: "So much evidence in there"
Attempted Revival and Final Shutdown
Despite initially shutting down their website and Telegram channel, OTP Agency attempted to revive their operations just days later. However, this revival was short-lived. The National Crime Agency (NCA) took the site offline less than a month later when the trio were arrested.
The Impact
According to NCA investigators, more than 12,500 people were targeted by OTP Agency users during the 18 months the service was active. The case highlights the ongoing threat of sophisticated phishing and fraud schemes.
Conclusion
The OTP Agency case serves as a cautionary tale for those involved in cybercriminal activities. While this particular service has been shut down, it demonstrates the potential profitability and risks associated with operating such platforms. The case highlights the importance of operational security and the need for constant adaptation in the face of law enforcement scrutiny.
Lessons for Cybercriminals
For those considering similar ventures:
- Be aware that high-profile services attract attention from both cybersecurity researchers and law enforcement.
- Understand that digital evidence can be difficult to completely erase, as seen in the incriminating chat logs.
- Recognize that attempting to revive operations after exposure significantly increases the risk of arrest.
- Consider that even seemingly anonymous online services can be traced back to their operators.
The cybercriminal landscape is constantly evolving, with law enforcement agencies becoming increasingly sophisticated in their tracking and prosecution methods. While new opportunities for illicit gains may arise, the risks of detection and severe legal consequences continue to grow.
Remember, engaging in cybercrime carries serious legal and personal risks. The allure of quick profits must be weighed against the potential for long-term imprisonment and the destruction of one's future prospects.