Fixxx
Moder
- Joined
- 20.08.24
- Messages
- 1,042
- Reaction score
- 4,023
- Points
- 113

«Keyboards of Honor, OPPO, Samsung, Vivo and Xiaomi smartphones allow network eavesdropping».
Such alarming headlines have circulated in the media over the past weeks. The source of this information is a rather serious study on vulnerabilities in keyboard traffic encryption. Malefactors capable of monitoring network traffic, for instance through an infected home router, can indeed intercept every key press and uncover all passwords and secrets. But don't rush to switch your Android to an iPhone - it only concerns input in Chinese using the pinyin system and under the condition that the "cloud prediction" feature is activated. However, it's worth investigating the situation with other keyboards from different manufacturers.
Why are many pinyin keyboards vulnerable to eavesdropping?
The pinyin input method editor (IME), also known as the Chinese phonetic alphabet, allows conveying Chinese words using Latin characters and diacritical marks. This is the official romanization system for Chinese adopted by the UN. For smartphones where drawing characters is not very convenient pinyin is a very popular input method used by over a billion people according to some estimates. Unlike many other languages word prediction for Chinese (especially in pinyin input) is challenging to implement directly on a smartphone - it's a computationally intensive task. Therefore almost all keyboards (or more precisely, input methods) use cloud predictions meaning they send the entered pinyin characters to a server at the moment of input and receive recommendations for completing the word. Sometimes the cloud function can be disabled but this decreases the speed and quality of input in Chinese.
To predict the input text in pinyin the keyboard sends data to the server.
Naturally, due to the cloud prediction system all the characters entered are accessible to the keyboard developers. But not only to them! Character-by-character data exchange requires specific encryption which many developers implement incorrectly. As a result all key presses and response predictions can be easily deciphered by unauthorized parties. Details on each of the discovered vulnerabilities can be found in the original source, but overall, out of the nine analyzed keyboards only the pinyin input method editor (pinyin IME) on Huawei smartphones implemented correctly encrypted TLS and withstood attacks. However, the input methods of Baidu (Baidu IME), Honor, iFlytek, OPPO, Samsung, Tencent, Vivo and Xiaomi were found to be vulnerable to varying degrees with the standard pinyin keyboard on Honor (Baidu 3.1) and pinyin QQ not receiving updates even after the research authors contacted the developers. Pinyin users are advised to update their input method editor (IME) to the latest version and (in case of no updates) to download another pinyin input method.
Do other keyboards send key presses?
There's no direct technical need for this. Predicting word endings and sentences for most languages can be done directly on the device, so there's no need for character-by-character data transmission in popular keyboards. However, data on entered texts may be sent to a server for synchronizing personal dictionaries between devices for machine learning and other purposes unrelated to the keyboard's primary function such as advertising analytics. Would you like to have such data stored on Google and Microsoft servers? It's a matter of personal choice. However, hardly anyone is interested in sharing this data with unauthorized individuals. At least one such incident was disclosed in 2016: the SwiftKey keyboard "distinguished" itself by predicting email addresses and other elements from the personal dictionary of other users. Following the incident Microsoft temporarily disabled the synchronization service presumably to rectify the issues. If you don't wish to store your personal dictionary on Microsoft servers don't create a SwiftKey account and (if you already have one) disable it and delete the cloud-stored data following the instructions.
No other widely known cases of leaked entered texts have been noted. However, studies have shown that popular keyboards actively monitor metadata during input. For instance, Google's Gboard and Microsoft's SwiftKey send data about each entered word: language, word length, precise input start time and the app where the word was entered. SwiftKey also sends statistics on your effort savings: how many words were entered in full, how many were automatically predicted and how many were swiped. Given that both keyboards send a unique advertising identifier to the server it creates broad possibilities for profiling - for example, it allows identifying which users are communicating with each other on any messenger. If you create a SwiftKey account and don't disable the "Help Microsoft improve products" option then, judging by the privacy policy, "small fragments of entered text" may be sent to the server. How this works and how significant these "small fragments" are is unknown.
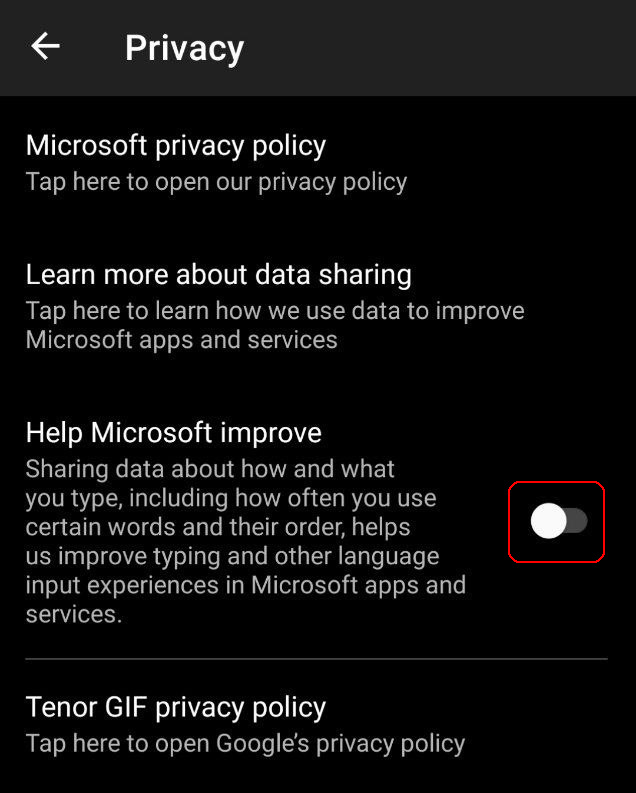
«Help Microsoft improve... What? Data collection?»
Google allows disabling the Share Usage Statistics option in Gboard significantly reducing the amount of transmitted information - it doesn't include the apps where the keyboard was used and word lengths.
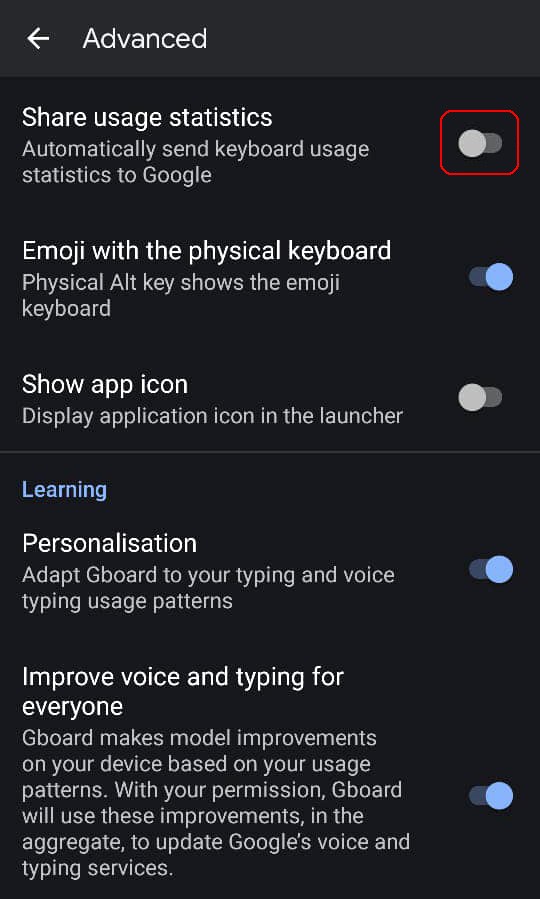
By disabling the Share Usage Statistics option in Gboard you will significantly reduce the amount of information collected.
From a cryptography perspective data exchange in Gboard and SwiftKey didn't raise concerns among researchers as both applications rely on standard TLS implementation in the operating system and are resistant to common cryptographic attacks. Therefore, intercepting traffic for these applications is unlikely. Alongside Gboard and SwiftKey the authors also analyzed the popular application AnySoftKeyboard. It fully justified its reputation as a privacy-conscious keyboard and does not transmit any telemetry to servers.
Is it possible for confidential data to leak from a smartphone?
To intercept crucial data an application doesn't have to be a keyboard. For example, TikTok monitors all data copied through the clipboard even though this feature seems unnecessary for social networks. Malware on Android often activates special capabilities and administrator rights on smartphones to capture data from input fields and directly from files of "interesting" applications. On the other hand an Android keyboard may leak not only typed texts. For instance, the ai.type keyboard caused data leakage from 31 million of it's users. It inexplicably collected data such as phone numbers, precise geolocation and even the contents of the address book.
How to protect against monitoring?
- Use a keyboard that doesn't transmit excessive data to servers. Before installing a new keyboard application search online for information about it by name - if there were any scandals related to it they will surface immediately.
- Go through all its settings and disable all possible ways of synchronization and data transmission. These may be hidden under various names including "Account", "Cloud", "Help to improve products…" and even "Sending audio donations".
- Check the permissions required by the keyboard on Android and revoke any unnecessary ones. Access to contacts, camera or something like this is definitely not needed for a keyboard.
- Install applications only from trusted sources check the application's reputation and don't grant it excessive permissions.


