Fixxx
Moder
- Joined
- 20.08.24
- Messages
- 1,038
- Reaction score
- 4,023
- Points
- 113

If you are concerned about the security of your wireless network your worries may not be unfounded.
Many routers have a default setting, that makes your WPA/WPA2-protected Wi-Fi network vulnerable.
In this post we will discuss one of the most dangerous methods of hacking wireless networks that exploit this setting and how to protect yourself from it.
The most effective attack on WPA/WPA2-PSK: PMKID capture.
PMKID capture is the most efficient, simple to execute and completely unnoticed by the victim method of attacking wireless networks protected by WPA/WPA2 standards. The essence of this attack is that it allows for the interception of encrypted Wi-Fi passwords that wireless routers constantly broadcast, even when no devices are connected to them. By obtaining the encrypted password the attacker can use a brute-force method to decrypt it and thus connect to the Wi-Fi network. This attack can also be performed on a mass scale using a technique called wardriving. In this scenario the hacker drives around the city in a car or on a motorcycle, scanning all available wireless networks and intercepting their encrypted passwords that routers broadcast. The equipment needed for this is minimal: just a laptop, a long-range Wi-Fi adapter and a powerful antenna.
The intercepted encrypted passwords can be cracked on the go. However, a more effective approach is to unload all the captured data onto a high-performance computer after the drive and run a password cracking tool. The effectiveness of this attack was demonstrated in Hanoi: a Vietnamese hacker scanned about 10,000 Hanoi wireless networks and was able to decrypt the passwords for half of them.
Why does the Wi-Fi attack using PMKID capture work?
Why do wireless routers broadcast Wi-Fi passwords encrypted in the air albeit in encrypted form? The reason is that it's a standard function of the 802.11r standard, which is implemented in most routers and usually enabled by default. This standard describes a mechanism for fast roaming in Wi-Fi networks that use multiple access points. To speed up the reconnection of client devices to new access points, they constantly broadcast their identifier - the PMKID. This identifier is a derivative of the PMK (Pairwise Master Key). More precisely, it contains the result of calculating the SHA-1 hash function where the PMK key and some additional data are used as input. The PMK key, in turn, is derived from the Wi-Fi password - once again, the result of calculating the SHA-1 hash function from this password.
In simple terms, the PMKID contains the Wi-Fi network password in a doubly hashed form. In theory, the hashing process is irreversible meaning that it's impossible to recover the original data from the resulting hash value. Presumably, the creators of the 802.11r standard relied on this when devising the fast roaming mechanism using PMKID. However, hashed data can be cracked by brute-force. This is especially aided by the fact that people rarely use truly secure passwords for wireless networks often relying on predictable character combinations. This was apparently overlooked by the creators of 802.11r. This problem was discovered a few years ago by a team behind one of the most popular utilities for password recovery (or simply put, for hacking) - Hashcat. Since then, specialized tools have been developed specifically for cracking intercepted PMKID.
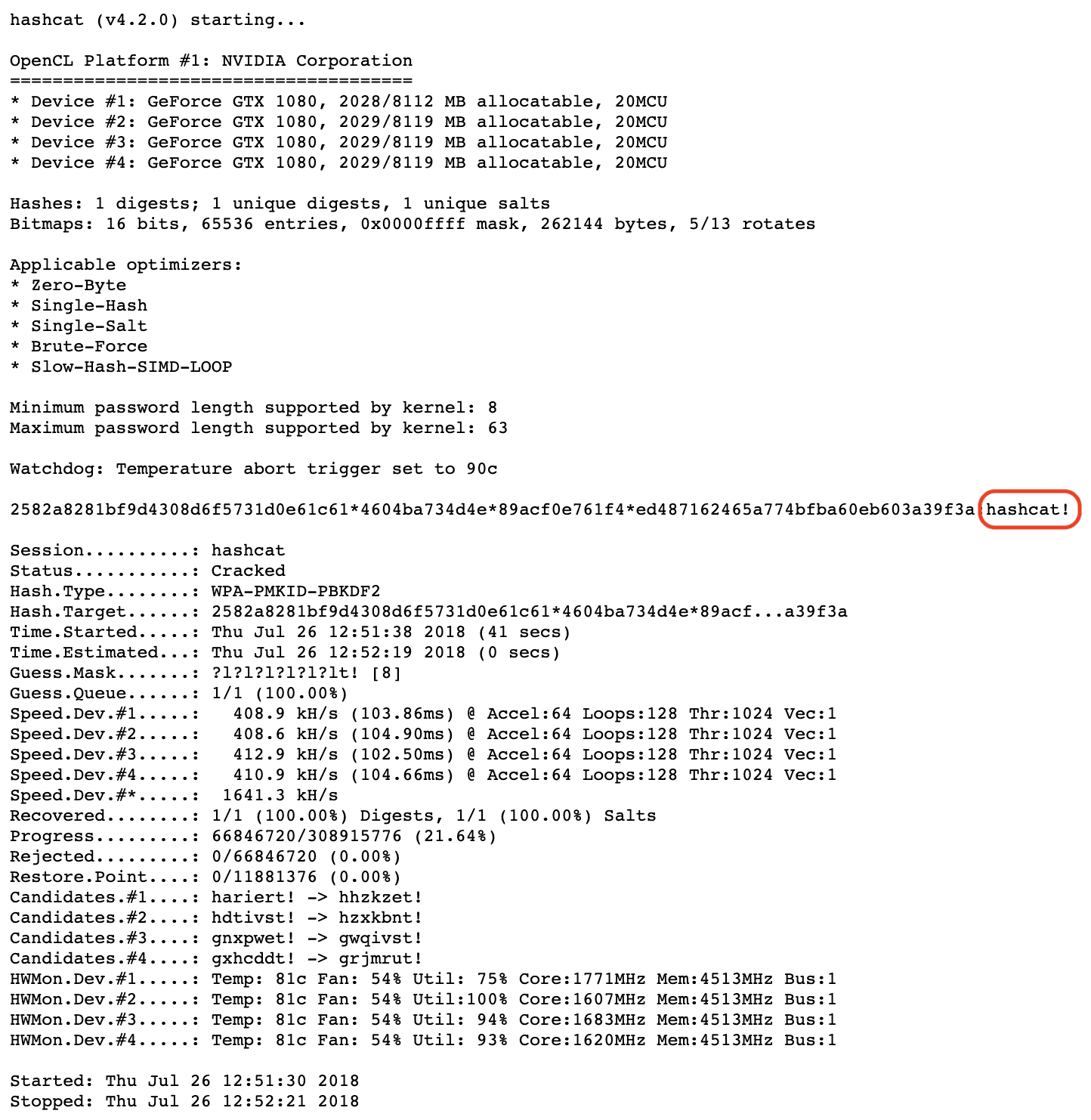
*successful extraction of the password "hashcat!" from a wireless network from captured PMKID
Therefore, in practice the attacker typically intercepts the PMKID which contains the encrypted password and then uses a dictionary attack - a process of trying common passwords collected in a database.
How to protect your Wireless Network from PMKID capture attack?
Fortunately, there are several protective measures that are not too difficult to implement in practice:
- Come up with the longest and most complex password possible for your wireless network. The PMKID attack allows for the interception of an encrypted Wi-Fi password but it still needs to be decrypted. The more complex the password, the less likely it's that attackers will succeed.
- Disable PMKID transmission in the router settings. Unfortunately, not all routers allow you to do this but it's worth at least trying to find this setting. You can search for it using the terms PMKID or 802.11r.
- Switch to WPA. If all your devices support a newer Wi-Fi security standard consider switching to it: WPA3 is generally much more secure than WPA2 and, in particular, isn't vulnerable to PMKID capture attacks.
- Set up a guest network. Entering a secure password for the main network on new devices can be cumbersome, so set up a guest network with a simpler password. The guest network can also host potentially insecure devices like IoT devices.


