Fixxx
Moder
- Joined
- 20.08.24
- Messages
- 1,042
- Reaction score
- 4,023
- Points
- 113

In the implementations of the Bluetooth protocol for Android, macOS, iOS and Linux a vulnerability has been discovered that allows devices to be hacked remotely.
So let's talk about it...
The vulnerability in Bluetooth allows connecting a fake keyboard.
The essence of the problem is that a vulnerable device can be forced to connect to a fake Bluetooth keyboard without user confirmation bypassing checks by the part of the operating system responsible for the Bluetooth protocol. The corresponding authentication-free connection mechanism is specified in the Bluetooth protocol and vulnerabilities in specific implementations of the Bluetooth stack in popular operating systems allow attackers to exploit this mechanism. Subsequently, this connection can be used to input commands that allow performing any actions on the targeted device on behalf of the user without requiring additional authentication such as entering a password or using biometrics (fingerprint, facial recognition, etc.). According to security researcher Mark Newlin who discovered this vulnerability, no special equipment is required for a successful attack - a laptop with Linux and a standard Bluetooth adapter is sufficient. As one might guess, the attack is naturally limited by the Bluetooth interface: the attacker must be in close proximity to the victim. This excludes a truly widespread exploitation of the discovered vulnerability but attacks using this method can pose a threat to individuals who are of special interest to hackers.
Which devices and operating systems are vulnerable?
This vulnerability affects a range of operating systems and several classes of devices based on them, albeit in slightly different ways. Depending on the OS used, devices may be more or less vulnerable.
Android
Devices based on Android were most thoroughly examined for the presence of the vulnerability described above. Mark Newlin tested seven smartphones with different versions of the operating system: Android 4.2.2, Android 6.0.1, Android 10, Android 11, Android 13 and Android 14 - and found that all of them are susceptible to Bluetooth hacking. Moreover, in the case of Android all that is needed for the hack is Bluetooth enabled on the device. The researcher informed Google about the discovered vulnerability in early August. In turn, the company has already released patches for Android versions 11-14 and sent them to smartphone and tablet manufacturers using this OS who are expected to create and distribute the corresponding security updates to their customers' devices. Of course, these patches must be installed as soon as they become available for your devices based on Android 11/12/13/14. Until then, to protect against hacking it's advisable to keep Bluetooth turned off. For devices running older versions of Android no updates are planned - they will remain vulnerable to this attack indefinitely, so the advice to disable Bluetooth will remain relevant for them until the end of their service life.
MacOS, iPadOS, iOS
Regarding Apple's operating systems the researcher didn't have such a wide range of test devices. Nevertheless he was able to confirm that the vulnerability exists in iOS 16.6 as well as in two versions of macOS - Monterey 12.6.7 (x86) and Ventura 13.3.3 (ARM). It can be assumed with a high degree of certainty that a wider range of versions of macOS and iOS as well as related systems like iPadOS, tvOS and watchOS are actually vulnerable to Bluetooth attacks. Another piece of bad news: the new Apple security feature introduced this year (the Lockdown Mode) doesn't protect against attacks using the Bluetooth vulnerability. This applies to both iOS and macOS.
Here's a reminder of how to correctly turn off Bluetooth in iOS:
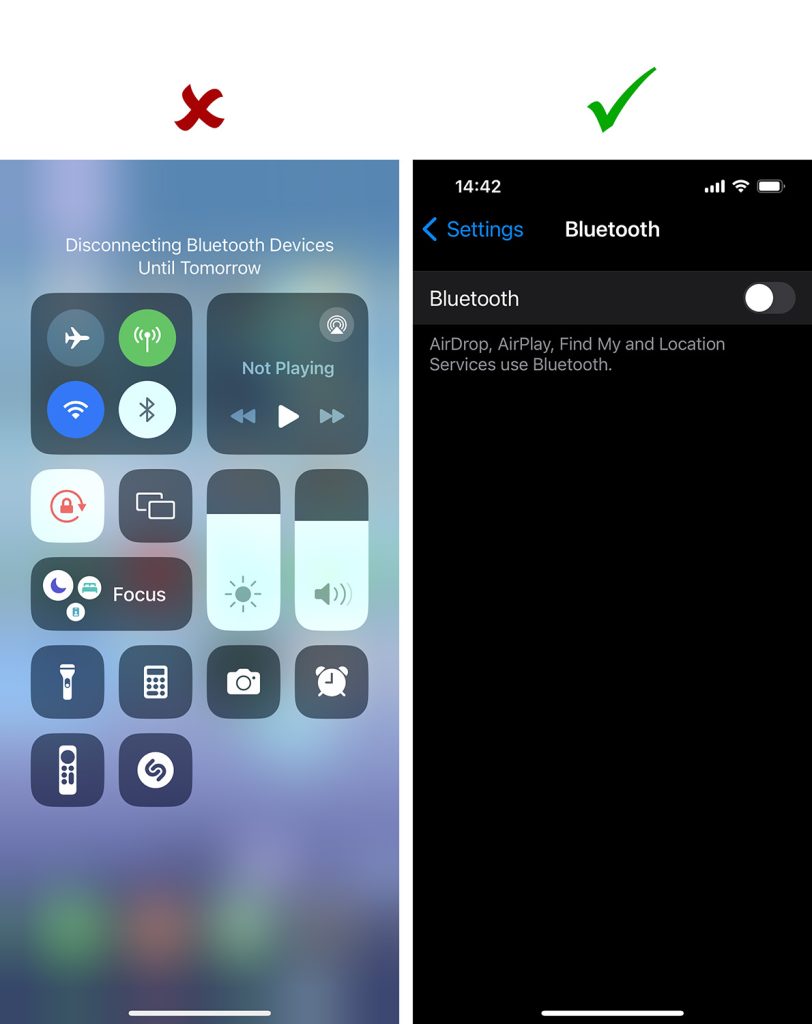
It should be done through the settings, not the Control Center!
Fortunately, for a successful attack on Apple operating systems, in addition to having Bluetooth enabled an additional condition must be met: the device must be paired with an Apple Magic Keyboard. This means that Bluetooth attacks primarily pose a threat to Macs and iPads used with a wireless keyboard. The likelihood of hacking an iPhone through this vulnerability is apparently negligible. The researcher informed Apple about the discovered bug around the same time as Google but the company hasn't yet provided information on security updates and a detailed list of vulnerable OS versions.
Linux
This attack also works for BlueZ - the Bluetooth stack included in the official Linux kernel. Mark Newlin confirmed the presence of the Bluetooth vulnerability in Ubuntu Linux versions 18.04, 20.04, 22.04 and 23.10. The bug that enables the attack was discovered and fixed back in 2020 (CVE-2020-0556). However, this fix was disabled by default in most popular Linux distributions and only enabled in ChromeOS (as per information received from Google). The vulnerability discovered by the researcher for Linux has been assigned the CVE-2023-45866 number and, according to Red Hat, has a 7.1 out of 10 (CVSS v3) severity rating and a "moderate" threat status. To successfully exploit this vulnerability the only condition that must be met is that the Bluetooth discovery or connection capabilities must be enabled on the Linux device.
The good news is that a patch for this vulnerability is already available - it's recommended to install it as soon as possible. Read more about Bluetooth Security.
Last edited:

