Fixxx
Moder
- Joined
- 20.08.24
- Messages
- 1,042
- Reaction score
- 4,023
- Points
- 113
The article is created to allow users to analyze the anonymity of their presence and provide more detailed information about the verification methods.
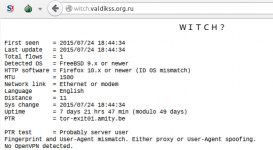
First, go to BrowserLeaks (or similar). We'll talk about 14 verification methods:
1. HTTP proxy headers
Some proxies append their headers to the request initiated by the user's browser. Often this is the real IP address of the user. Make sure that if the proxy server writes anything in the headers listed below, at least it's not your address:
HTTP_VIA, HTTP_X_FORWARDED_FOR, HTTP_FORWARDED_FOR, HTTP_X_FORWARDED, HTTP_FORWARDED, HTTP_CLIENT_IP, HTTP_FORWARDED_FOR_IP, VIA, X_FORWARDED_FOR, FORWARDED_FOR, X_FORWARDED, FORWARDED, CLIENT_IP, FORWARDED_FOR_IP, HTTP_PROXY_CONNECTION
2. Open ports of HTTP proxy
The IP address from which the request to our page came can reveal a lot. For example, you can see which ports are open on the other side? The most burnt ports: 3128, 1080 and 8123. If you avoid using them you can easily avoid unwarranted suspicions of using 3proxy, SOCKS 5 or Polipo.
3. Open ports of web proxy
As with HTTP you can assign a web proxy to any port but we wanted the test to run very quickly, so we limited it to reverse connects on ports 80 and 8080. Is a web page returned? Great! At the moment, we can identify PHProxy, CGIProxy, Cohula and Glype. Non-standard ports with authentication close the issue.
4. Suspicious hostname
Having an IP address you can try to resolve the client's hostname. Stop words that may hint at a tunnel: vpn, hide, hidden, proxy. It's not advisable to associate domain names with personal VPNs, and if you do, it's better to avoid "speaking" names.
5. Difference in time zones (browser and IP)
Based on GeoIP data you can determine the country by the user's IP and consequently, their time zone. Then you can calculate the time difference between the browser and the time corresponding to the VPN server's time zone. Is there a difference? Then the user is likely hiding. For Russia there's no exact database of latitude and longitude for regions and since there are many time zones we don't consider these addresses in the final result. With European countries it's the opposite - they are easily exposed. When switching to a VPN don't forget to adjust the system time, change the time in the browser or work with proxies.
6. IP belonging to the Tor network
If your IP address is a Tor node from the site's list - congratulations! You have been exposed.
Nothing criminal but the fact of revealing that you are hiding is not very pleasing.
7. Turbo browser mode
By collecting IP address ranges of Google, Safari, Opera and comparing them to the user's address you can assume the use of traffic compression services in browsers of these companies. Usually these services also leak your real address in the headers. Don't rely on traffic compression as an anonymity tool.
8. Web proxy detection (JS method)
By comparing window.location.hostname with the host of the requested page you can determine if a web proxy is being used.
Web proxies (our anonymizers) are generally unreliable, so it's best to avoid such anonymization methods altogether.
9. IP leakage through Flash
Adobe Flash works very well bypassing user proxies. By initiating a connection to our server you can determine the user's IP. By running a special daemon that logs all incoming connections with key tags you can learn a lot. The best way not to disclose your address is to not use Adobe Flash at all or disable it in the browser settings. For example, the Firefox browser disables Flash by default, so it's worth considering.
10. Tunnel detection (two-way ping)
By pinging the client's IP from our server side you can determine the approximate route length. The same can be done from the browser side; XMLHttpRequest pulls an empty page from our nginx. A loop difference of more than 30 ms can be interpreted as a tunnel. Of course, the routes there and back may differ or the web server may slow down a bit, but overall, the accuracy is quite good. The only way to protect yourself is to block ICMP traffic to your VPN server by properly configuring your firewall.
11. DNS leak
Finding out which DNS a user is using is not a problem; we have written our DNS server that records all requests to our uniquely generated subdomains. The next step was to gather statistics on several million users who uses which DNS. We linked them to providers, discarded public DNS and obtained a list of DNS/ISP pairs. Now it's quite easy to find out if a user claims to be a subscriber of one network but uses DNS from another. Using public DNS services partially solves the problem.
12. Leakage through social networks
This is not an IP address leak but by sharing the names of authorized users left and right, for example, Facebook leaks private data that undermines all surfing anonymity. The "Logout" button after each session generally solves the issue but the best recommendation is not to use social networks...
13. WEB-RTC
WebRTC allows establishing video conferencing without using plugins through modern browsers like Mozilla and Chrome but at the same time reveals your real IP even when using a VPN as well as a list of all local IP addresses behind NAT. WebRTC is supported only in Chrome and Firefox browsers. There is no native support for WebRTC in Internet Explorer and Safari browsers.
Disabling WebRTC in Firefox:
Enter in the browser address bar: about:config
Enter in the search: media.peerconnection.enabled
Set the value to "false" and check again!
Disabling WebRTC in Chrome:
To block WebRTC in Google Chrome you need to install the WebRTC Block plugin.
Disabling WebRTC on Android for Chrome users:
In the Chrome browser address bar, enter: chrome://flags/#disable-webrtc
Set the value to "enable".
Another alternative way to detect proxies and VPNs: