Fixxx
Moder
- Joined
- 20.08.24
- Messages
- 1,042
- Reaction score
- 4,023
- Points
- 113

Recently, researchers from the USA and China published a study proposing an extremely unusual method of stealing fingerprints. Imagine receiving a call from a malicious actor or connecting to a conference call from your smartphone where an attacker has access. During the call you perform actions on your phone, naturally swiping your finger across the screen. The sound of such movements is well-audible through the built-in microphones of smartphones meaning a potential attacker can record and analyze this sound. From this they can reconstruct certain fragments of a fingerprint which can be sufficient to unlock your smartphone using an "artificial finger". Just think about it: from these "rustles" one can deduce the pattern on the fingertip, making it a fantastically beautiful attack through external channels!
How to steal a fingerprint through sound?
The general scheme of the new PrintListener attack is shown in the image:
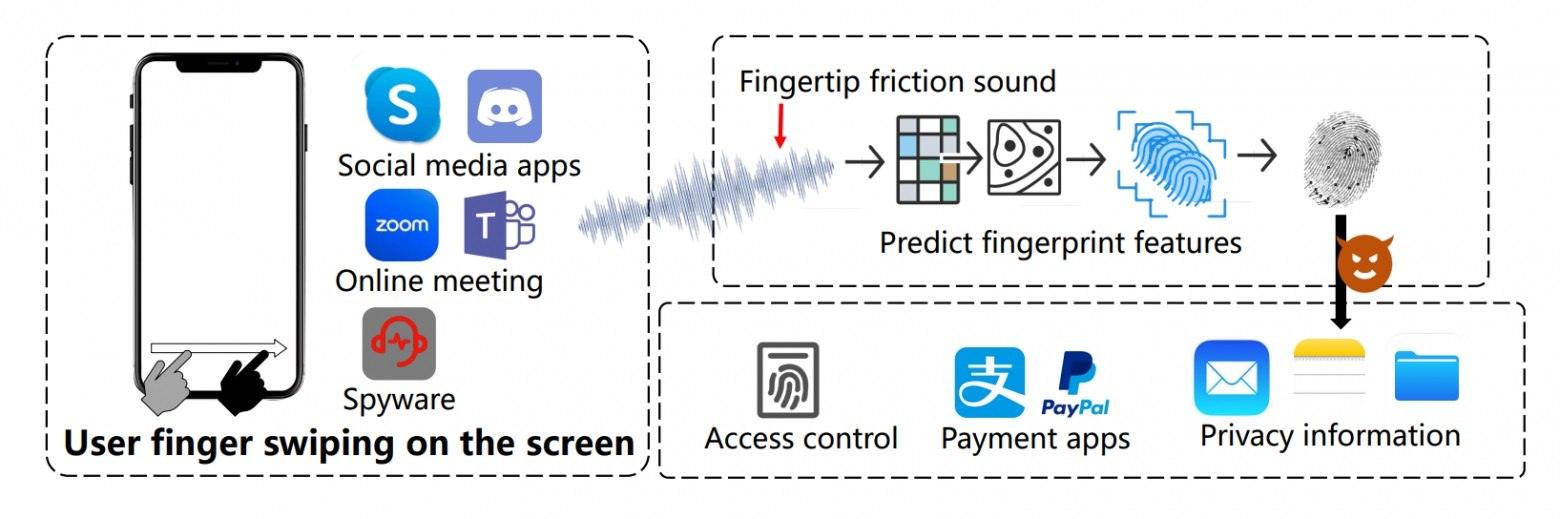
If the potential victim swipes their finger across the screen during a call the attacker can reconstruct fingerprint elements from the sound. When a user swipes their finger across the screen they produce an almost inaudible noise to the human ear. These roughly speaking "rustles" are non-uniform - their characteristics change when larger nodes in the fingerprint pattern, such as "loops" and "arches" touch the screen. If the noise is recorded using a sensitive microphone and later analyzed based on the data obtained one can reconstruct the approximate location and pattern of such nodes.
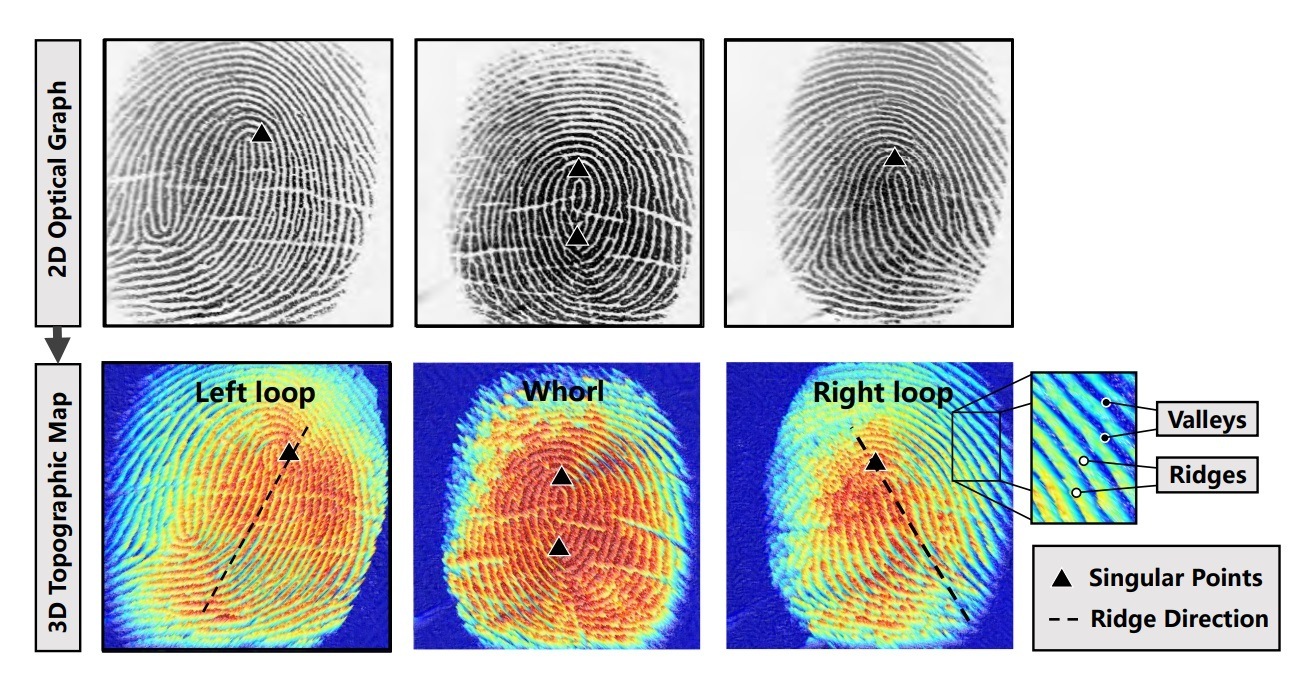
Prominent elements of the fingerprint pattern are crucial for determining whether the scanned fingerprint matches a previously stored one. To make the attack somewhat realistic the authors of the new study did extensive work. Firstly, they created an automated system to search for sounds resembling the rustling of a finger moving across the screen, eliminating the need to manually search for these relatively quiet and rapid events. Secondly, they created a large database containing photos of fingerprints and the corresponding sounds of finger movements on the display in different directions with varying background noise for different smartphone models and so on. In total, 65 volunteers participated in the experiment and 180 fingerprints were scanned. These data were processed using a machine learning algorithm. The trained algorithm was able to predict certain characteristics of the fingerprint fairly confidently solely based on the sound of finger movement on the smartphone surface.
Effectiveness of the PrintListener attack.
PrintListener is not the first type of attack on fingerprint scanners. In 2017 a research paper was published where a random fingerprint was applied to the scanner instead of a real user's and in some cases it worked! Why? In many modern smartphones the fingerprint scanner is embedded in the power button which is quite narrow. By definition, such a scanner only sees a fragment of the fingerprint. Furthermore, scanners are designed to focus on the prominent elements of the fingerprint pattern.
If a synthetic finger with a loop roughly matching a loop on a real fingerprint is detected the scanner may authorize the user! This attack was named MasterPrint.
Another important parameter in the operation of a scanner is the false positive rate. An ideal fingerprint scanner should only accept the applied finger in the case of a 100% match with the pattern. However, using such a sensor would be impractical! Each time a user applies their finger slightly differently - at a different angle slightly higher or lower. The finger can be dry or wet, dirty or damaged. To account for the imperfections of the real world the scanner is adjusted to grant access not only in cases of exact matches but also in situations where it "almost matches the template". This inevitably leads to false positives: when another person's finger is applied but the scanner thinks it is "as it should be". The typical percentage of such unwanted detections ranges from 0.01% (in the strictest case) to 1%. The latter option would be more convenient to use but it increases the likelihood that someone else will apply their finger to someone else's smartphone and the device will be unlocked. The MasterPrint attack showed that a synthetic fingerprint with a common element like a "loop" triggered in 2.4–3.7% of cases with partial recognition right from the first attempt. If multiple attempts are possible the probability of false positives increases. In the experiments 12 consecutive attempts passed the fake fingerprint in 26–30% of cases! In these experiments the false positive rate was 0.1%.
The PrintListener attack builds on the ideas laid out in the 2017 MasterPrint study. Processing audio information allows for reasonably confident identification of a significant node in the fingerprint pattern. It essentially enables an attacker to target fingerprint scanners not randomly but using a reconstructed node based on sound. The attacker can then print a finger with a synthetic fingerprint incorporating the predicted significant element. With an acceptable false positive rate of 0.1% the PrintListener attack successfully deceived fingerprint scanners in 48–53% of cases. Even in a more stringent scenario with an acceptable false positive rate of 0.01% the biometric scanner could still be hacked in 7.8–9.8% of cases. This is significantly more effective than the MasterPrint attack. Moreover, in all cases no more than 5 attempts were made to scan the synthetic finger aligning with the real limitations on biometric authentication in the same smartphones.
The benefits and drawbacks of biometrics.
We have previously written about the traditional risks associated with fingerprint scanners. In short, it should never be considered an entirely reliable means of authentication. It's relatively easy to steal your fingerprint using traditional methods. People leave fingerprints on surfaces and objects they touch. In some cases a usable fingerprint can even be extracted from a high-resolution photo taken from a reasonable distance of three meters. Simple scanners can be deceived by merely printing the biometric information stolen earlier on a printer. With modern ultrasonic sensors in smartphones located beneath the display, such a trick would not work but an artificial finger with the required pattern can be 3D-printed.
One common issue with any biometric authentication system is the difficulty of keeping such information secret. Unlike a password it's impossible to change a fingerprint.
The new study doesn't necessarily provide new reasons to worry about the security of our data. The imperfect nature of biometrics is already factored into the logic of how sensors work in our devices. Because fingerprints can be relatively easily "borrowed" or mistakenly recognized smartphones periodically prompt us to enter a PIN code or confirm an online purchase with a password. When combined with other security methods fingerprint scanners are decent. Such protection against unauthorized access is better than having none at all. Moreover, a simple digital unlock code can also be observed or guessed based on traces on the screen display. Nonetheless, the PrintListener attack turned out to be outstanding. Valuable fingerprint data was extracted from a seemingly inappropriate source. The attack scenario was quite realistic. It's conceptually similar to previous studies where passwords entered on a keyboard were recognized by sound. The lesson of this story is simpler than it seems:
Don't leave confidential information (especially business data) solely under the protection of biometrics!

